Newsroom

We Help Customers Design, Deploy, and Operate Their Public Key Infrastructure
If you would like more information about PKI or other related industry topics such as encryption, identity management, or two-factor authentication—or to schedule an interview with Mark B. Cooper, please contact us.
-
March 5, 2025
PKI Spotlight Unveils Industry-First Multi-Vendor HSM Monitoring Support
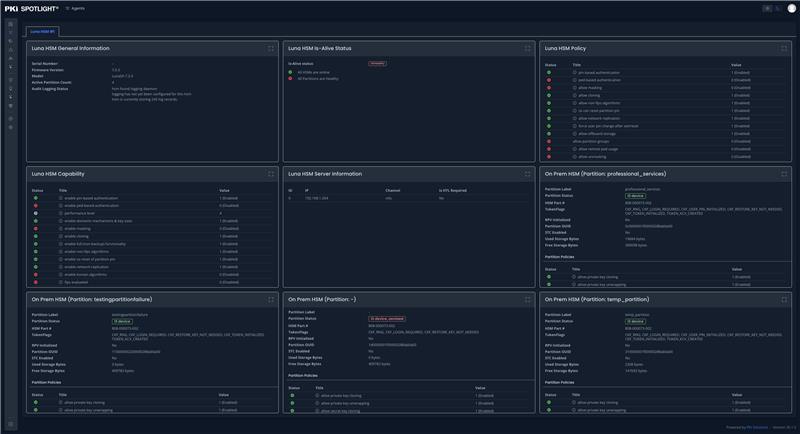
PKI Spotlight’s Multi-Vendor HSM Monitoring feature provides organizations with unified, real-time visibility into diverse Hardware Security Module (HSM) platforms, including both nCipher (Entrust) and Luna (Thales) HSMs, across on-premises and cloud environments.
Reading Time: < 1 minute -
October 16, 2024
PKI Spotlight Integrates PKI Maturity Model Self-Assessment by the PKI Consortium
PKI Solutions is proud to announce the integration of the PKI Maturity Model Self-Assessment from the PKI Consortium into PKI Spotlight, the cutting-edge platform for real-time Public Key Infrastructure (PKI) observability and management.
Reading Time: < 1 minute -
March 8, 2024
Disaster Recovery and Business Continuity: Leveraging Public Key Infrastructure for Utilities
Discover how PKI Solutions’ PKI Spotlight contributes to minimizing downtime for utilities during disaster recovery operations through real-time monitoring and alerting.
Reading Time: < 1 minute -
May 9, 2023
PKI Solutions Introduces New Features in PKI Spotlight to Address CISOs' workload, Mitigate Risks, Worry
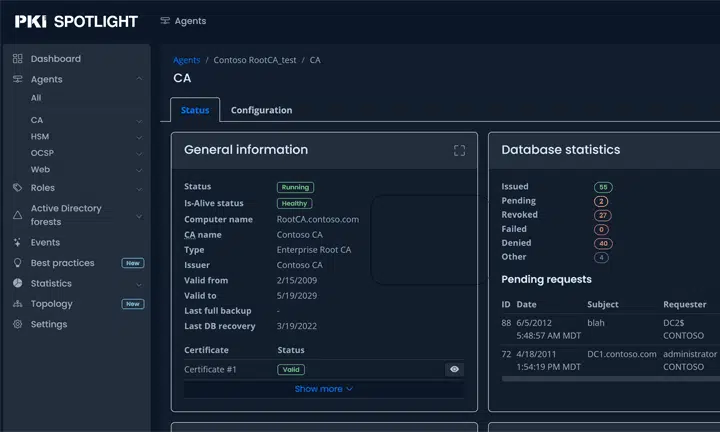
PKI Solutions has announced the latest release of PKI Spotlight, a Public Key Infrastructure monitoring and alerting solution designed to address specific, ongoing tasks that CISOs are responsible for in the current cybersecurity landscape.
Reading Time: < 1 minute -
October 26, 2022
PKI Spotlight updates help enterprises manage their PKI and HSM environments
ISARA Corp., the world's leading provider of quantum-safe security solutions, today announced that it is dedicating the intellectual property behind its ISARA Catalyst™ Agile Digital Certificate Methodology — including four patents — to the public. Industry leaders, including Crypto4A, DigiCert, Entrust, ISARA, Keyfactor, PKI Solutions, Sectigo, and Venafi.
Reading Time: < 1 minute -
July 14, 2022
PKI Spotlight updates help enterprises manage their PKI and HSM environments
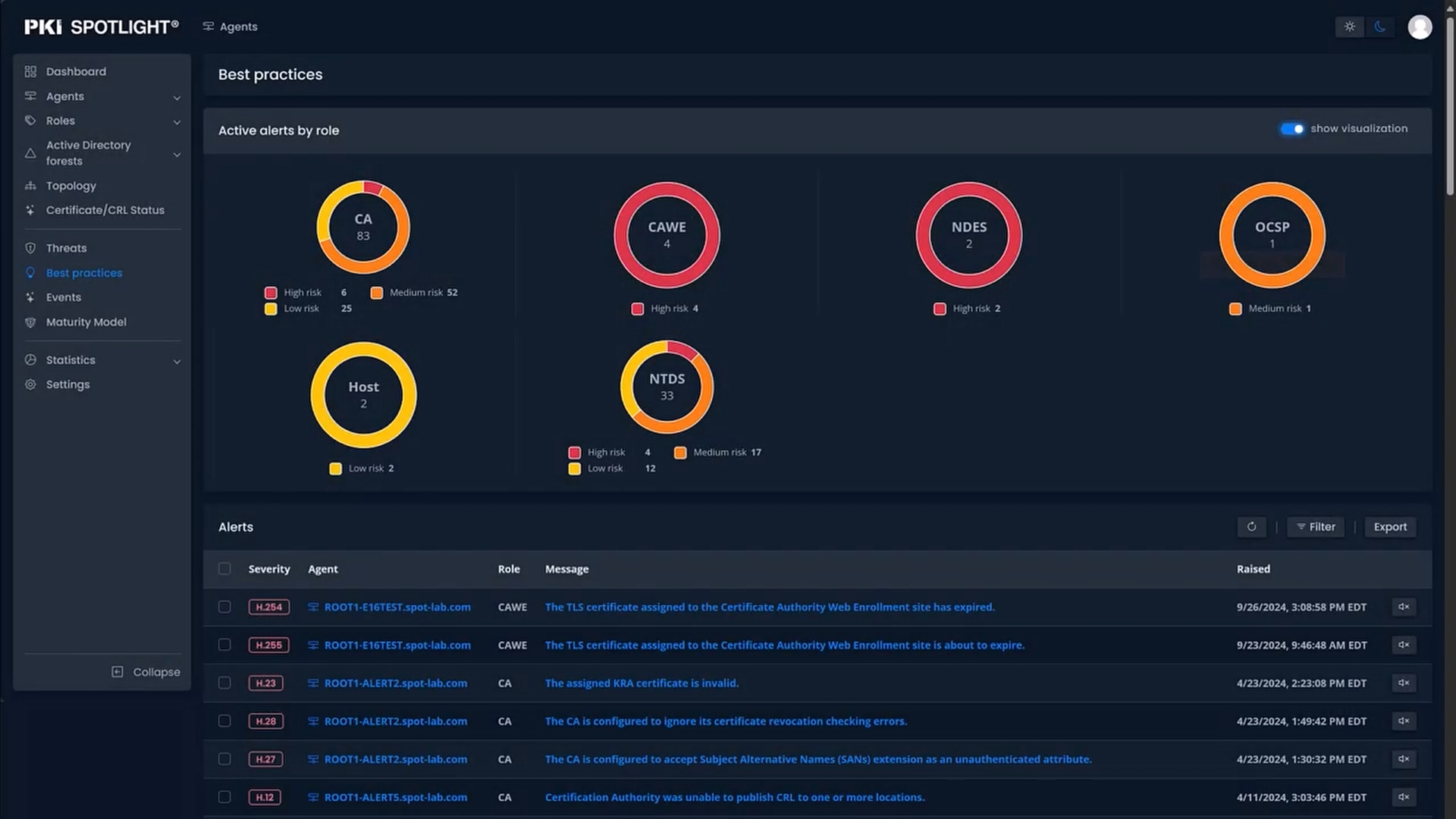
Real-time monitoring and alerting of the availability, configuration, and security of all PKI and Hardware Security Module (HSM) environments are consolidated into one easy-to-use dashboard.
Reading Time: < 1 minute -
July 14, 2022
PKI Spotlight updates help enterprises manage their PKI and HSM environments
New Is-Alive (not just looks alive) health checks detect failure conditions before they impact an organization’s PKI environment, potentially preventing millions of dollars in losses resulting from business disruptions.
Reading Time: < 1 minute
- 6
1 of 6
Media Resources
News Releases
- PKI Solutions Introduces Latest Version of PKI Spotlight
July 12, 2022 - PKI Solutions Announces New ‘Introduction to Certificates & Keys’ Training Course
April 11, 2022 - PKI Solutions Announces $2M Credit Facility from Northwest Bank
Mar 29, 2022 - PKI Solutions Introduces PKI Spotlight Monitoring and Alerting Solution
Mar 14, 2022
Background
- PKI Solutions Corporate Fact Sheet
- PKI Glossary Of Terms
- Microsoft PKI In-depth Training
- Advanced Microsoft PKI Training
- Global SHAKEN/STIR Framework

 Schedule a Demo
Schedule a Demo