Can you please create the blog for CDP, AIA, OCSP after renewing issuing CA. do we required to update renewed issuing certificate in each devices or end users before to expire existing certificate. cover all those topic also better if you consider Intune SCEP profile prospective for users.
Active Directory Certificate Services (ADCS) Certificate Authority Renewal Error
Certificate Authority Migration and Renewal
In the past year many enterprises have migrated their Microsoft ADCS based PKI Infrastructure from Windows Server 2012 R2 to a newer operating system. The most common path for the migration is backup & restore to a server with the same name or backup & restore to server with a new name. Both options are supported, and both will also result in a new SID for the new CA server object in Active Directory.
Error While Renewing ADCS Issuing CA Certificate
Clients often wait until after the migration to renew the CA certificate. The PKI team logs on to the CA and generates the renewal request, gets it signed by the Policy/Intermediate or Root CA, and when the updated issuing CA certificate is installed, a misleading error will pop up.
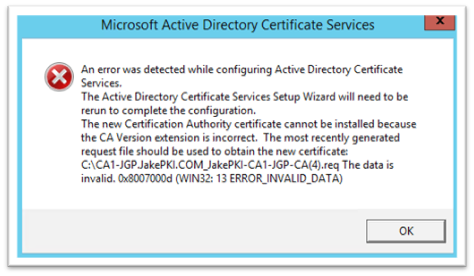
The data is invalid. 0x8007000d (WIN32: 13 ERROR_INVALID_DATA)

Expand Your PKI Visibility
Discover why seeing is securing with revolutionary PKI monitoring and alerting.
Learn More About PKI Spotlight®The Cause and Solution
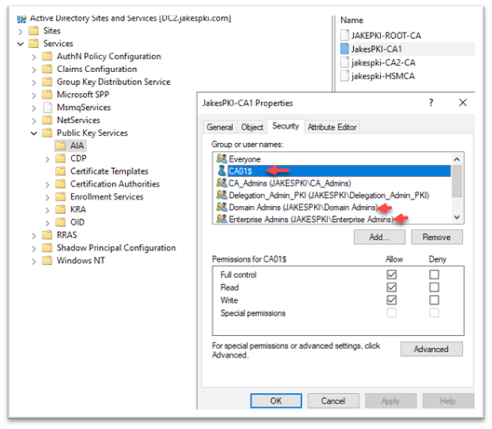
The error is misleading, and I have seen clients renew the CA certificate multiple times based on the misleading error message. First, if you have seen this message the renewal was successful at the CA level, but the CA was unable to update the CA object in Active Directory in the AIA container. This can be caused by a couple of different reasons. I mentioned above there is a new SID for the new CA server, even if the CA common name is the same. This will cause the current CA server object to not have access to update the CA object in the AIA container.
You want to make sure the current CA server’s machine account has access to the object. You also want to make sure the user logged on during the installation of the updated CA certificate is a domain or enterprise Administrator, or in a delegated group that has full control for installing the new certificate on the CA.
Other Considerations
There are other areas that should also be considered after a migration or issuing CA certificate renewal. The certificate revocation list (CRL) as well as the Online Responder (OCSP), Network Device Enrollment Service (NDES) configuration will also need to be checked and most likely updated. If you would like an additional blog on those topics, please let me know and I will get it created and posted.
Related Resources

Jake Grandlienard
Jake Grandlienard brings more than 19 years of industry experience as a senior level engineer. Jake is a subject matter expert in PKI, mobile device management software, smart card management software, and Hardware Security Module (HSM) integrations.
View All Posts by Jake GrandlienardComments
-
-
Hi Darshan,
Thanks for the topic suggestion! We can add this to our potential future blog topic list.
-

 Schedule a Demo
Schedule a Demo