Submitting Netscape SPKI (SPKAC) Cert Requests to ADCS
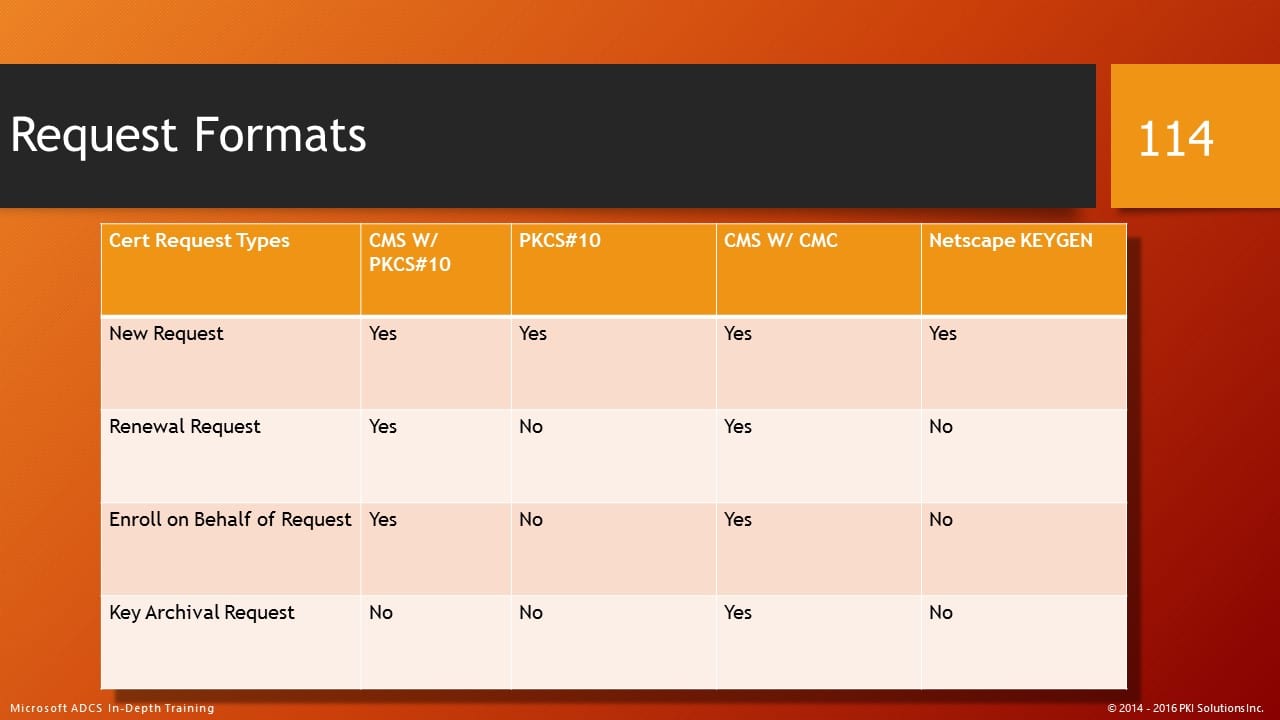
Recently I was contacted on Twitter with a question about Microsoft’s support of Signed Public Key and Challenge (Netscape SPKI) for certificate enrollment requests. I have long taught in my classes that there are a number of formats supported by ADCS for certificate requests. So I consulted one of the tables I talk about in my In-Depth PKI class. Here you can see that clearly the Netscape Keygen/SPKAC/SPKI is supported, but this person was reporting an error every time they submitted a request.

Expand Your PKI Visibility
Discover why seeing is securing with revolutionary PKI monitoring and alerting.
Learn More About PKI Spotlight®The errors were usually “wrong user password” or “error parsing request“. So we checked out all the usual items by reviewing the CSR itself – all looked fine. We ensured the request was being submitted by a valid user with the appropriate permissions on the template and the CA. All looked good. When we switched to another format the request went through just fine. The SPKAC is an older format and frankly there isn’t much documentation on it, but it is clearly “supported”. I even found a MSDN noted that it was a supported format for Certificate Enrollment Protocol.
So I reviewed the SPKAC format a little further and found that one key difference of this format is that in the SPKAC format there is a “challenge” phrase that is embedded into the CSR. This challenge is verified by the CA to ensure the CSR is unaltered, which is a bit redundant since the request is already signed. If you dump a SPKAC request, you will see that there is an encoded ChallengeString, for example:
ChallengeString: “E425252E9E8C6166642D1CC6586605A5817BED57”
0000 30 82 01 50 30 82 01 22 30 0d 06 09 2a 86 48 86 0..P0..”0…*.H.
0010 f7 0d 01 01 01 05 00 03 82 01 0f 00 30 82 01 0a …………0…
0020 02 82 01 01 00 99 e8 95 ae 94 cc 5f 89 91 38 31 ……….._..81
0030 95 54 76 06 72 93 46 6e 28 c9 86 8c f2 0e 5c a8 .Tv.r.Fn(…..\.
0040 80 c2 4b 35 d0 2a 10 d0 5a 16 f6 97 81 46 55 dd ..K5.*..Z….FU.
0050 6a 30 92 d1 5d e8 6f c0 7c 96 5c 65 d0 b1 91 2e j0..].o.|.\e….
0060 6a 50 ba 0e 05 71 43 d2 bb d0 e7 ee 90 f1 64 f4 jP…qC…….d.
0070 c4 05 d4 ba 19 13 a0 56 cd 99 57 a5 56 80 3a 83 …….V..W.V.:.
0080 ec d9 5c 77 79 9a 6a 36 34 63 5d d3 dd 35 cc f3 ..\wy.j64c]..5..
0090 f5 0c e2 d2 e1 dc 63 0c 77 f3 a0 ad e4 12 ee f5 ……c.w…….
00a0 f1 ef f1 25 26 7b 52 8f 54 2c 8c 01 03 e2 ca f8 …%&{R.T,……
00b0 9a cb bc 1c 51 32 2e 75 20 20 32 74 27 ee 20 5f ….Q2.u 2t’. _
00c0 00 c9 59 66 88 14 6f e0 97 ec 7f 18 ec 2c 8c e3 ..Yf..o……,..
00d0 10 e6 d7 3e 4c b2 6d 8a 09 c8 ff 6c b6 85 1c b0 …>L.m….l….
00e0 3c 27 fd 92 6f bc 5e 62 a5 b6 72 50 a9 21 da 30 <‘..o.^b..rP.!.0
00f0 1b fb 08 f7 5b d3 e2 aa 88 81 81 04 57 9e 89 88 ….[…….W…
0100 b3 f7 10 e2 1d 54 63 d4 ae ee 9d 30 37 fe 41 9f …..Tc….07.A.
0110 b5 56 fd 0f 73 75 6b c4 6d d1 da 71 94 50 c5 f7 .V..suk.m..q.P..
0120 0d 0f 1c ce 8b 02 03 01 00 01 16 28 45 34 32 35 ………..(E425
0130 32 35 32 45 39 45 38 43 36 31 36 36 36 34 32 44 252E9E8C6166642D
0140 31 43 43 36 35 38 36 36 30 35 41 35 38 31 37 42 1CC6586605A5817B
0150 45 44 35 37 ED57
So I reached out and did some research. It turns out that Microsoft hasn’t had SPKAC in it’s test suite for many years now and frankly it was unknown if it was even supported. But assuming it was still working, I needed to find the key to the submission process to get it to work. It turns out this format requires a very carefully crafted set of submission parameters to specify the challenge phrase.
Option #1
If the request contains no SPKAC challenge phrase, the certificate request will be accepted and processed normally.
Option #2
If the request contains a challenge, then the caller must submit the request with a matching challenge string included in the separate name-value pair strings passed to ICertRequest::Submit. This parameter string is formatted as follows: “name1:value1\nname2:value2”, where \n is a newline character that separates multiple name-value pairs. In this case: “Challenge:”. The challenge is compared as a case sensitive string. The web pages and certreq -submit are capable of adding request attribute name-value pair strings when submitting requests to the CA.
Once this was figured out, the SPKAC request, challenge phrase included, was successfully submitted to the CA and issued without any further problems. Since this is not documented anywhere else in Microsoft materials or on the web, this might be the only place where this is documented at all. Hopefully this will help anyone in the future faced with working with and processing SPKAC requests.
Related Resources

Mark B. Cooper
President & Founder at PKI Solutions, Leading PKI Cybersecurity Subject Matter Expert, Author, Speaker, Trainer, Microsoft Certified Master.
View All Posts by Mark B. Cooper
 Schedule a Demo
Schedule a Demo