-
Blog
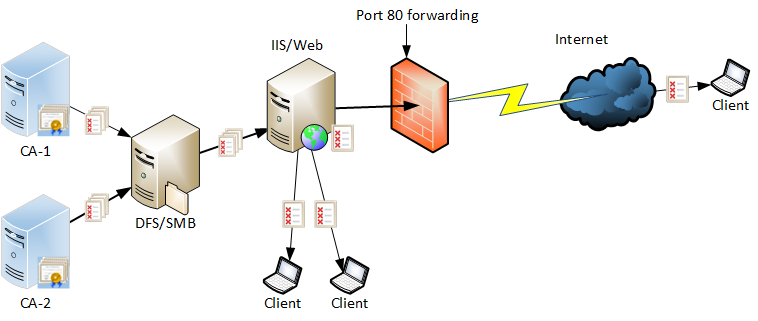
Creating Highly Available CDP and AIA Locations with Azure, Part 4
Learn how to create highly available CDP and AIA locations in Azure for improved PKI reliability. Part 4 of our expert guide.
-
Blog
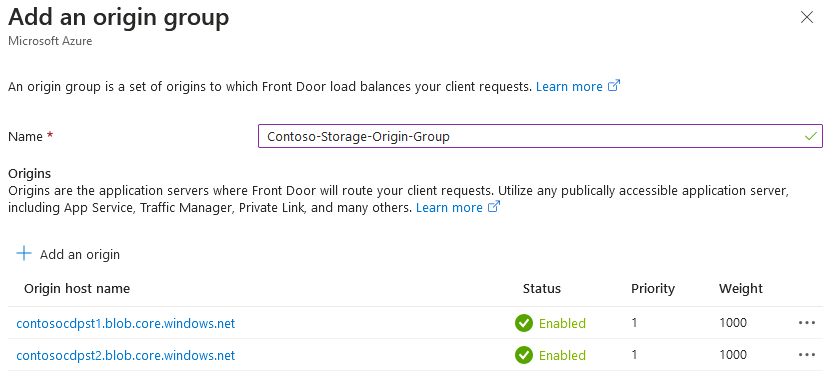
Creating Highly Available CDP and AIA Locations with Azure, Part 3
Learn how to create highly available CDP and AIA locations in Azure for improved PKI reliability. Part 3 of our expert guide.
-
Blog
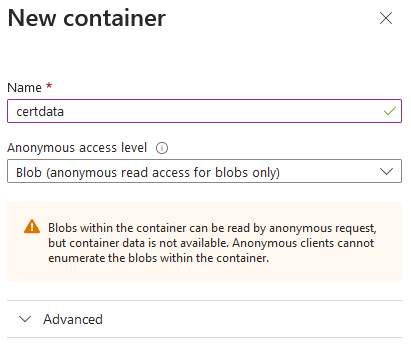
Creating Highly Available CDP and AIA Locations with Azure, Part 2
Learn how to create highly available CDP and AIA locations in Azure for improved PKI reliability. Part 2 of our expert guide.
-
Blog
Creating Highly Available CDP and AIA Locations with Azure, Part 1
Learn how to create highly available CDP and AIA locations in Azure for improved PKI reliability. Part 1 of our expert guide.

-
Blog
Understanding Active Directory Certificate Services Containers in Active Directory
Explore the key roles of Active Directory Certificate Services Containers in enhancing PKI systems and security infrastructure.
1 of 6

