-
Blog
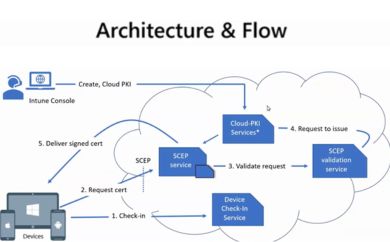
PKI Insights Recap – Microsoft Intune Cloud PKI
Explore how Microsoft Intune enhances PKI security via cloud integration, improving digital certificate management and protection.
- 9
9 of 22
Explore how Microsoft Intune enhances PKI security via cloud integration, improving digital certificate management and protection.
9 of 22