Operational Best Practice Checks for Certificate Templates
Best Practices to prevent Certificate Database bloat and reduce operational overhead.
View All PKI Spotlight® FeaturesBest Practices to Prevent Cert DB Bloat and Un-used (potentially expensive) Certificates
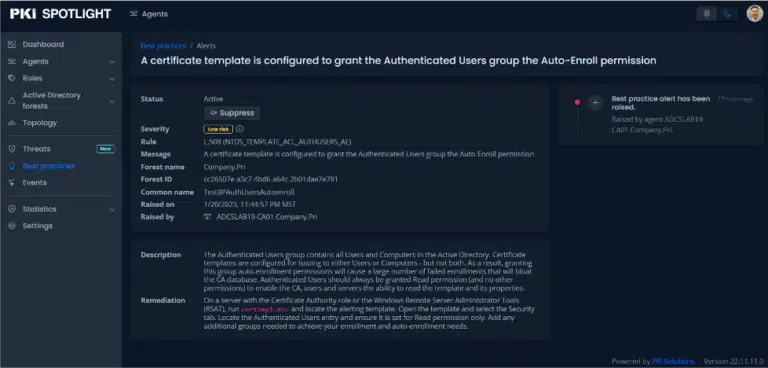
Template ACL has authenticated users and auto-enroll
This Best Practice checks if a template allows all authenticated users (machine and users) to auto-enroll. This setting can lead to less privileged users enrolling in a template designed for a specific function. It also leads to failed requests unnecessarily bloating the certificate database. The bigger the cert DB, the longer it takes for the PKI to shut down and start up.
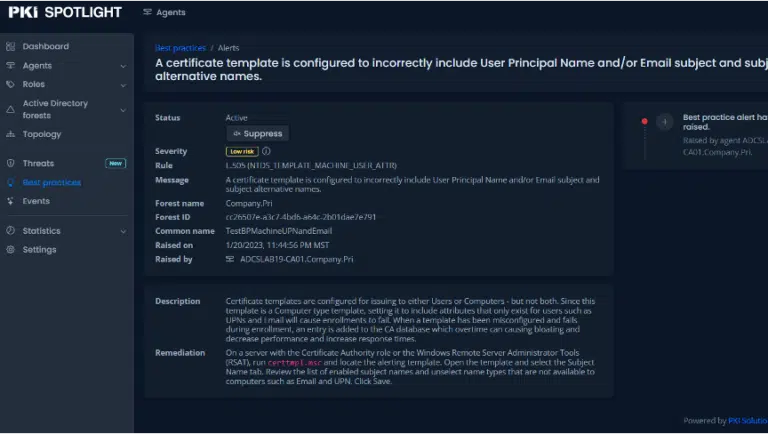
Template is machine context and SAN properties enable Email, UPN
Machine objects in Active Directory normally do not have an assigned email or User Principal Name (UPN). Email and UPN are attributes of user objects, A machine context template (templates that will be enrolled by machines) that specifies Subject Alternative Name (SAN) properties to include Email and/or UPN will cause that certificate to fail upon enrollment. This failure is not a one-time event; the failed certificate requests will be repeated until the template is remediated. In the meantime, the certificate DB becomes clogged with potentially millions of failed requests.
This is another instance that leads to bloated certificate Databases lengthening maintenance tasks such as patching or Disaster Recovery drills. In most scenarios, PKI admins do not anticipate long DB startup and shutdown times which can lead to admins inadvertently corrupting the cert DB by prematurely terminating the startup process.
Best Practices to Reduce Operational Overhead
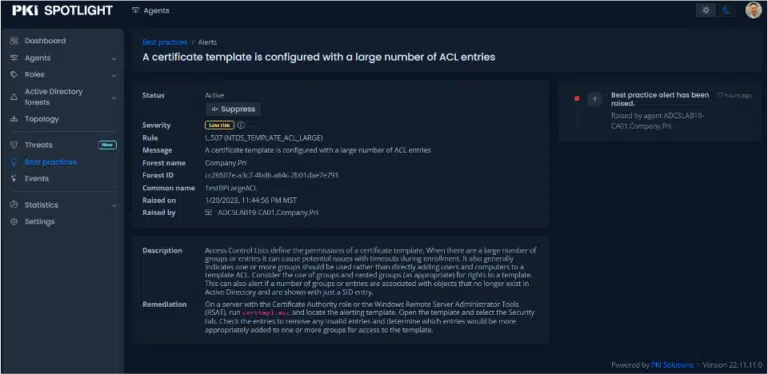
Template ACL count > 10
Certificate templates should have as small an access control list (ACL) as possible. Large ACLs create an operational burden on PKI and provisioning staff. The recommended Best Practice is to create security groups, populate devices and/or users into those groups and assign permissions on certificate templates to those groups. This check raises the flag for PKI admins to review certificate template permissions and work with the IAM team to assign permissions in a manner which is more sustainable in a provisioning/deprovisioning workflow.
Connect With Us for Certainty in Security
If you’re ready to learn more about our essential solutions for your essential PKI, reach out today. Book time with one of our specialists to discuss your needs and how we can meet and exceed your business requirements.
CONTACT US
Email: hello@pkisolutions.com
Phone: +1 (971) 231-5523
Corporate Headquarters
5331 S. Macadam Ave, Suite 330
Portland, Oregon 97239

 Schedule a Demo
Schedule a Demo