Issues with In-Place Upgrade of Windows OCSP Server
Recently, a client reached out after experiencing issues with an in-place upgrade of a Windows OCSP server. After the upgrade, the Online Responder had a bad signing certificate and would not request a new one.
This is a unique case, as the Online Responder server was using a Luna HSM for key protection and had a custom identity set for the Online Responder Service (OcspSvc). After the upgrade, we found the Online Responder Service was set to the default Network Service. This is an issue when using a Luna HSM, since the account used to interact with the Luna HSM must be defined/registered in KSPConfig.
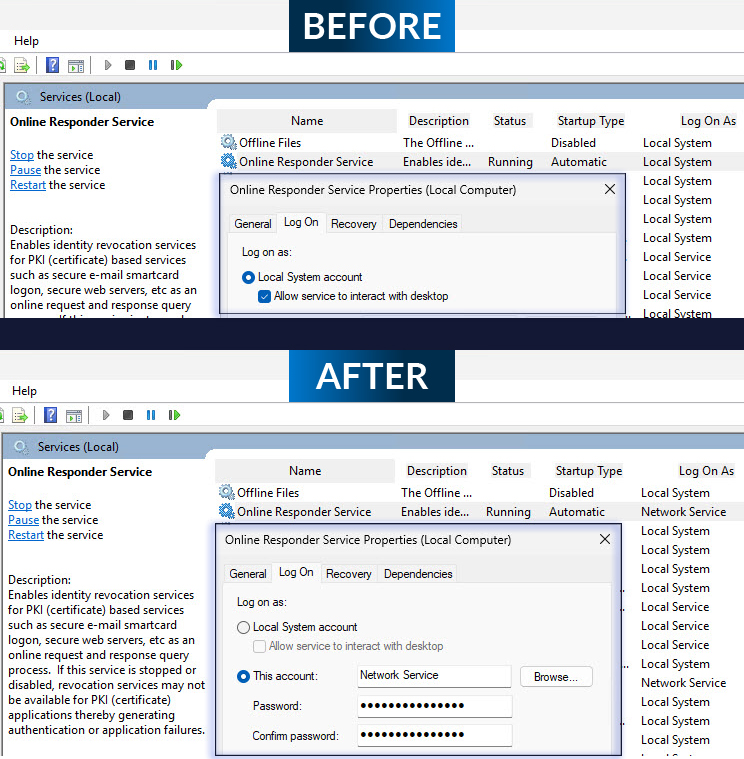
There are a couple of solutions that could have been used. The first is to set the Online Responder Service back to run under the custom account. The second would be to register the Network Service account via KSPConfig so it has access to interact with the Luna HSM protecting the Online Responder private keys.

See What You’re Missing
Check Out PKI SpotlightOne last quick note: If your organization is utilizing Luna HSMs to protect Online Responder private keys. Be aware that the default 14-day validity period can eventually fill the Luna partition, causing an outage. Consider extending the validity period of the Online Responder certificate template, or operational guide with steps to manually delete keys from the Luna partition at set intervals.
Thank you to Dhananjay for working through the issue and resolution and for confirming it is repeatable.
Please share your questions or comments.
—Jake

Jake Grandlienard
Jake Grandlienard brings more than 19 years of industry experience as a senior level engineer. Jake is a subject matter expert in PKI, mobile device management software, smart card management software, and Hardware Security Module (HSM) integrations.
View All Posts by Jake Grandlienard
 Schedule a Demo
Schedule a Demo