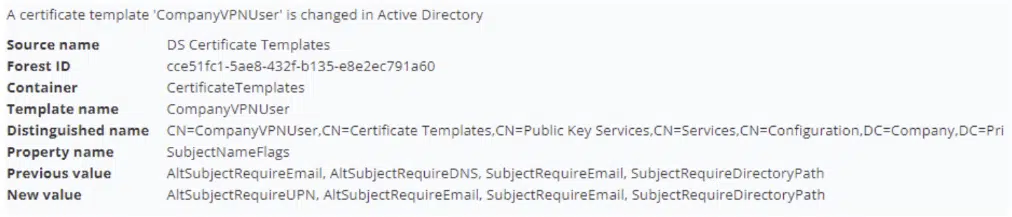
Excellent Article, Mike!
Here’s a little bit more info and a neat little lightly documented trick. If you run the command:
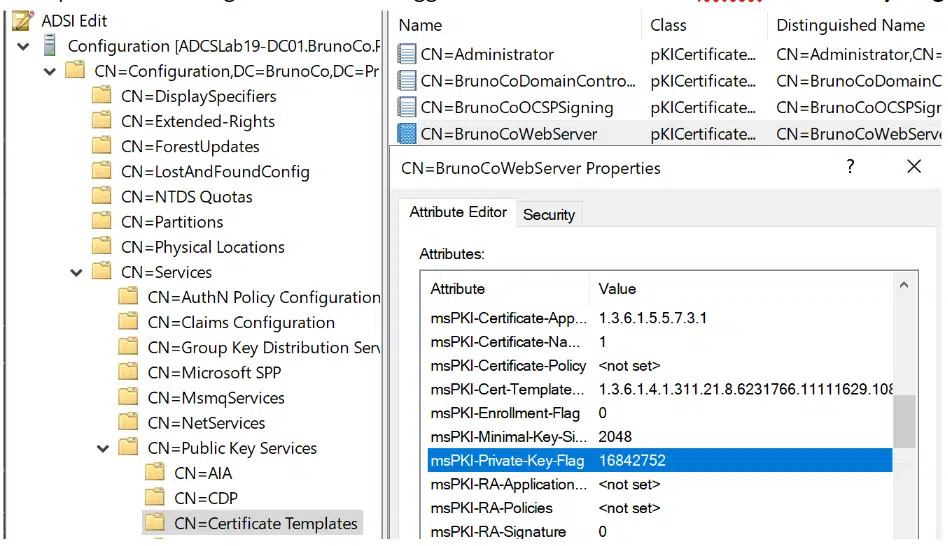
certutil -v -dstemplate [templateName]
the output will show the symbolic enumeration of that attribute and the flag names show they are preparing for potential changes in the future…
msPKI-Private-Key-Flag = “67371024” 0x4040010
(CTPRIVATEKEY_FLAG_REQUIRE_PRIVATE_KEY_ARCHIVAL — 1)
CTPRIVATEKEY_FLAG_EXPORTABLE_KEY — 10 (16)
(CTPRIVATEKEY_FLAG_STRONG_KEY_PROTECTION_REQUIRED — 20 (32))
(CTPRIVATEKEY_FLAG_REQUIRE_ALTERNATE_SIGNATURE_ALGORITHM — 40 (64))
(CTPRIVATEKEY_FLAG_REQUIRE_SAME_KEY_RENEWAL — 80 (128))
(CTPRIVATEKEY_FLAG_USE_LEGACY_PROVIDER — 100 (256))
(CTPRIVATEKEY_FLAG_EK_TRUST_ON_USE — 200 (512))
(CTPRIVATEKEY_FLAG_EK_VALIDATE_CERT — 400 (1024))
(CTPRIVATEKEY_FLAG_EK_VALIDATE_KEY — 800 (2048))
CTPRIVATEKEY_FLAG_ATTEST_NONE — 0
(CTPRIVATEKEY_FLAG_ATTEST_PREFERRED — 1000 (4096))
(CTPRIVATEKEY_FLAG_ATTEST_REQUIRED — 2000 (8192))
(CTPRIVATEKEY_FLAG_ATTEST_WITHOUT_POLICY — 4000 (16384))
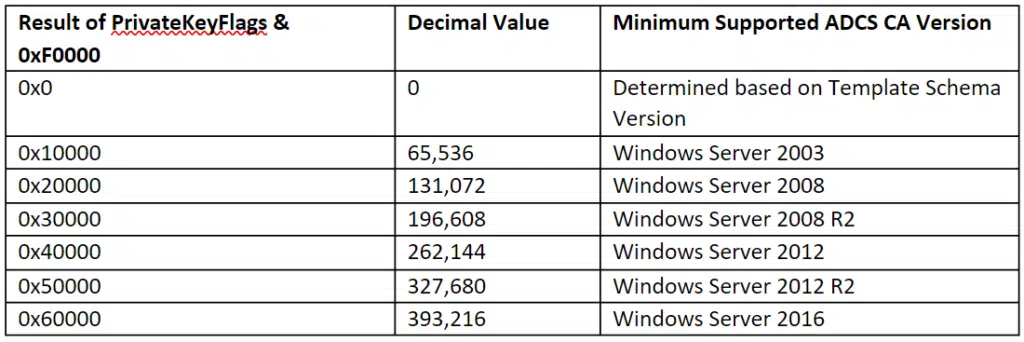
(TEMPLATE_SERVER_VER_NONE<<CTPRIVATEKEY_FLAG_SERVERVERSION_SHIFT — 0)
(TEMPLATE_SERVER_VER_2003<<CTPRIVATEKEY_FLAG_SERVERVERSION_SHIFT — 10000 (65536))
(TEMPLATE_SERVER_VER_2008<<CTPRIVATEKEY_FLAG_SERVERVERSION_SHIFT — 20000 (131072))
(TEMPLATE_SERVER_VER_2008R2<<CTPRIVATEKEY_FLAG_SERVERVERSION_SHIFT — 30000 (196608))
TEMPLATE_SERVER_VER_WIN8<<CTPRIVATEKEY_FLAG_SERVERVERSION_SHIFT — 40000 (262144)
(TEMPLATE_SERVER_VER_WINBLUE<<CTPRIVATEKEY_FLAG_SERVERVERSION_SHIFT — 50000 (327680))
(TEMPLATE_SERVER_VER_THRESHOLD<<CTPRIVATEKEY_FLAG_SERVERVERSION_SHIFT — 60000 (393216))
(V7<<CTPRIVATEKEY_FLAG_SERVERVERSION_SHIFT — 70000 (458752))
(V8<<CTPRIVATEKEY_FLAG_SERVERVERSION_SHIFT — 80000 (524288))
(V9<<CTPRIVATEKEY_FLAG_SERVERVERSION_SHIFT — 90000 (589824))
(V10<<CTPRIVATEKEY_FLAG_SERVERVERSION_SHIFT — a0000 (655360))
(V11<<CTPRIVATEKEY_FLAG_SERVERVERSION_SHIFT — b0000 (720896))
(V12<<CTPRIVATEKEY_FLAG_SERVERVERSION_SHIFT — c0000 (786432))
(V13<<CTPRIVATEKEY_FLAG_SERVERVERSION_SHIFT — d0000 (851968))
(V14<<CTPRIVATEKEY_FLAG_SERVERVERSION_SHIFT — e0000 (917504))
(V15<<CTPRIVATEKEY_FLAG_SERVERVERSION_SHIFT — f0000 (983040))
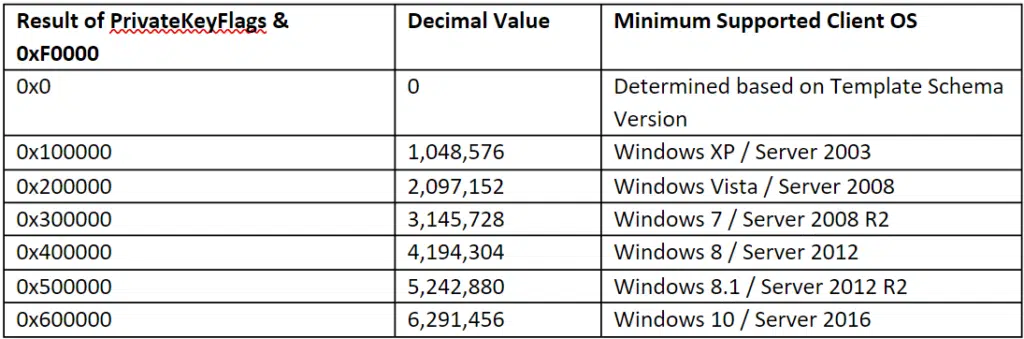
(CTPRIVATEKEY_FLAG_HELLO_KSP_KEY — 100000 (1048576))
(CTPRIVATEKEY_FLAG_HELLO_LOGON_KEY — 200000 (2097152))
(TEMPLATE_CLIENT_VER_NONE<<CTPRIVATEKEY_FLAG_CLIENTVERSION_SHIFT — 0)
(TEMPLATE_CLIENT_VER_XP<<CTPRIVATEKEY_FLAG_CLIENTVERSION_SHIFT — 1000000 (16777216))
(TEMPLATE_CLIENT_VER_VISTA<<CTPRIVATEKEY_FLAG_CLIENTVERSION_SHIFT — 2000000 (33554432))
(TEMPLATE_CLIENT_VER_WIN7<<CTPRIVATEKEY_FLAG_CLIENTVERSION_SHIFT — 3000000 (50331648))
TEMPLATE_CLIENT_VER_WIN8<<CTPRIVATEKEY_FLAG_CLIENTVERSION_SHIFT — 4000000 (67108864)
(TEMPLATE_CLIENT_VER_WINBLUE<<CTPRIVATEKEY_FLAG_CLIENTVERSION_SHIFT — 5000000 (83886080))
(TEMPLATE_CLIENT_VER_THRESHOLD<<CTPRIVATEKEY_FLAG_CLIENTVERSION_SHIFT — 6000000 (100663296))
(V7<<CTPRIVATEKEY_FLAG_CLIENTVERSION_SHIFT — 7000000 (117440512))
(V8<<CTPRIVATEKEY_FLAG_CLIENTVERSION_SHIFT — 8000000 (134217728))
(V9<<CTPRIVATEKEY_FLAG_CLIENTVERSION_SHIFT — 9000000 (150994944))
(V10<<CTPRIVATEKEY_FLAG_CLIENTVERSION_SHIFT — a000000 (167772160))
(V11<<CTPRIVATEKEY_FLAG_CLIENTVERSION_SHIFT — b000000 (184549376))
(V12<<CTPRIVATEKEY_FLAG_CLIENTVERSION_SHIFT — c000000 (201326592))
(V13<<CTPRIVATEKEY_FLAG_CLIENTVERSION_SHIFT — d000000 (218103808))
(V14<<CTPRIVATEKEY_FLAG_CLIENTVERSION_SHIFT — e000000 (234881024))
(V15<<CTPRIVATEKEY_FLAG_CLIENTVERSION_SHIFT — f000000 (251658240))
Be ready to figure out what V7-15 end up being…

 Schedule a Demo
Schedule a Demo