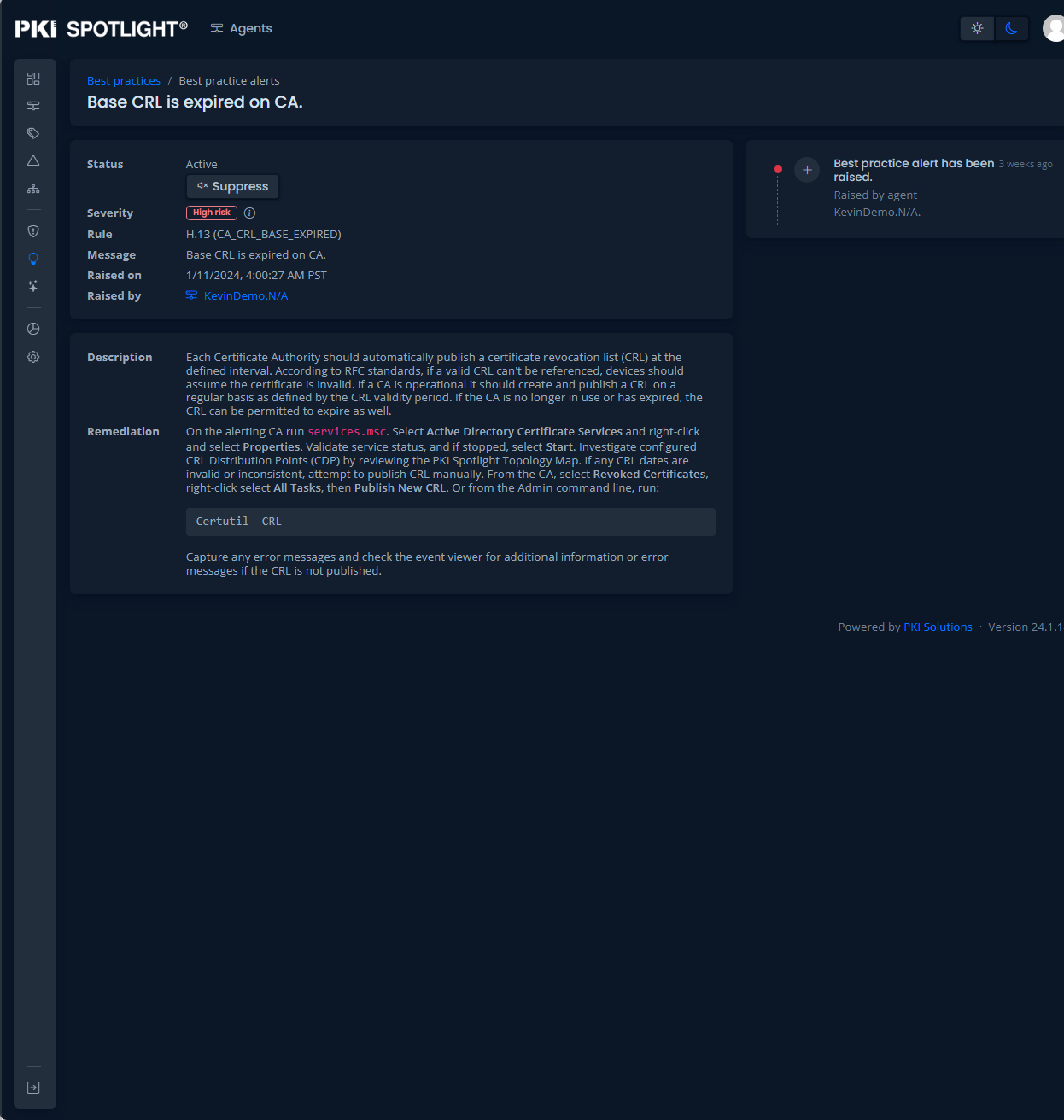
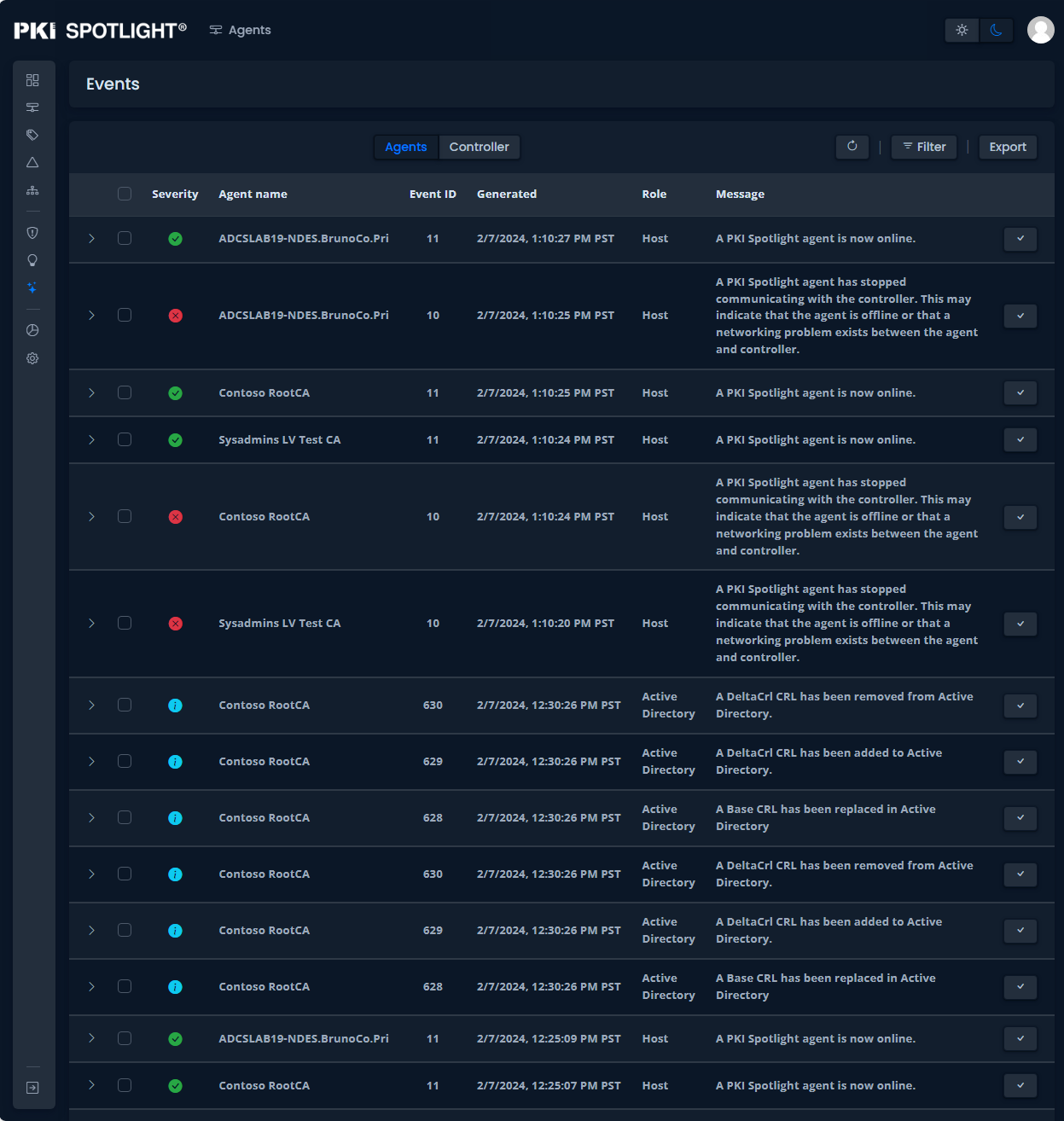
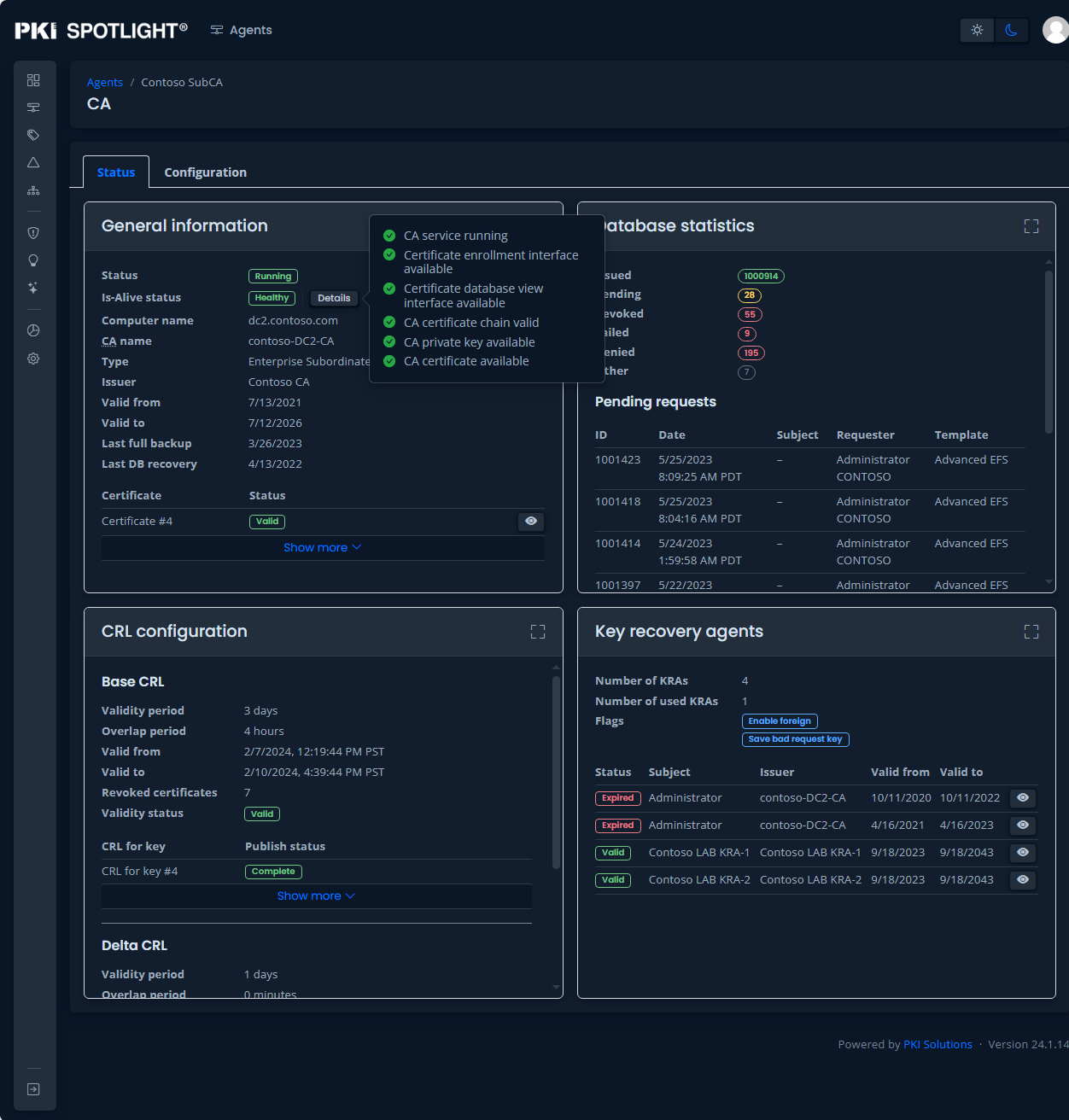
Expand PKI Visibility with PKI Spotlight®
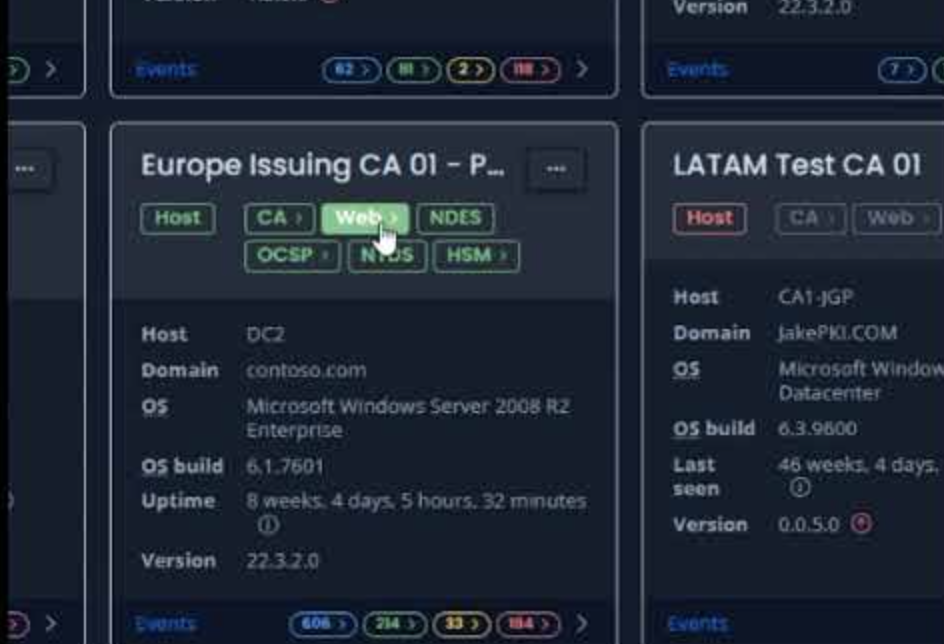
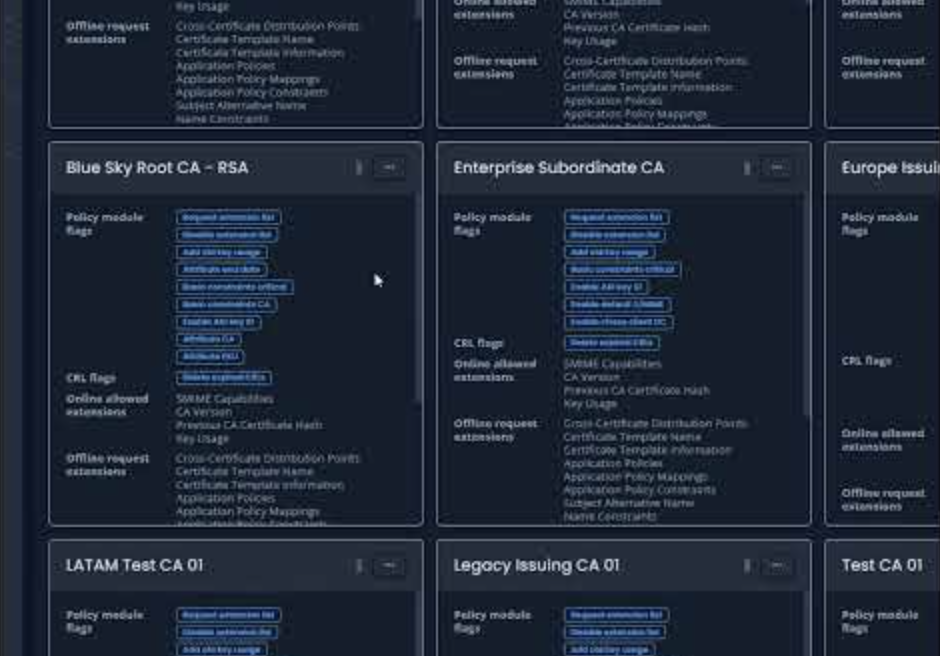
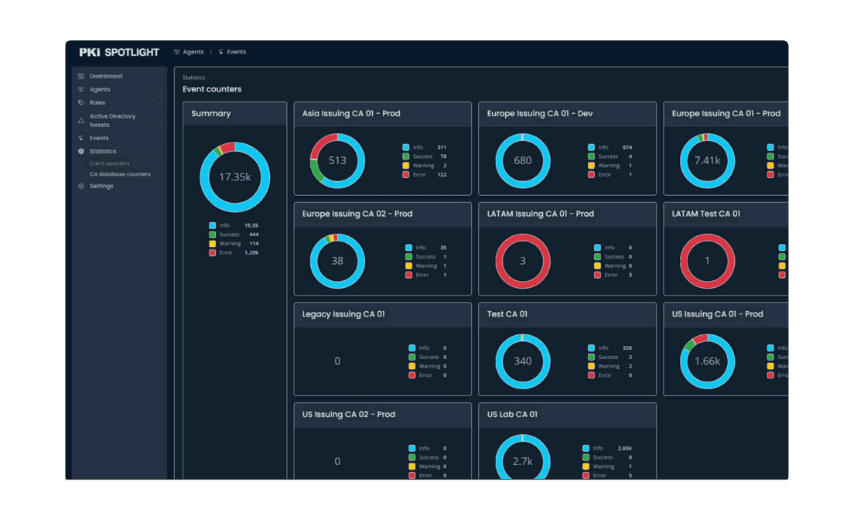
In cybersecurity, visibility is key. PKI Spotlight enables unmatched visibility across enterprise public key infrastructures and hardware security modules. This real-time monitoring software provides vital perspective into all PKI environments in one place to improve security, availability, and recoverability to keep you ahead of threats.
Schedule a Product Demo Download the Datasheet-
Seeing is Securing
PKI Spotlight turns experience into action. This unified visibility platform is built on PKI Solutions’ 20 years of experience identifying and remediating every type of PKI obstacle and environment, turning retroactive remediation into proactive visibility.
- Pre-detect configuration and availability issues before they cause certificate outage issues
- Act decisively and respond with urgency with complete insight into PKI configurations
- Review, refine and revamp PKI with operational and configurations best practices built on our extensive PKI expertise
- Improve Post-Quantum Readiness through discovery, identification, and alerting of non-compliant configurations throughout your PKI.
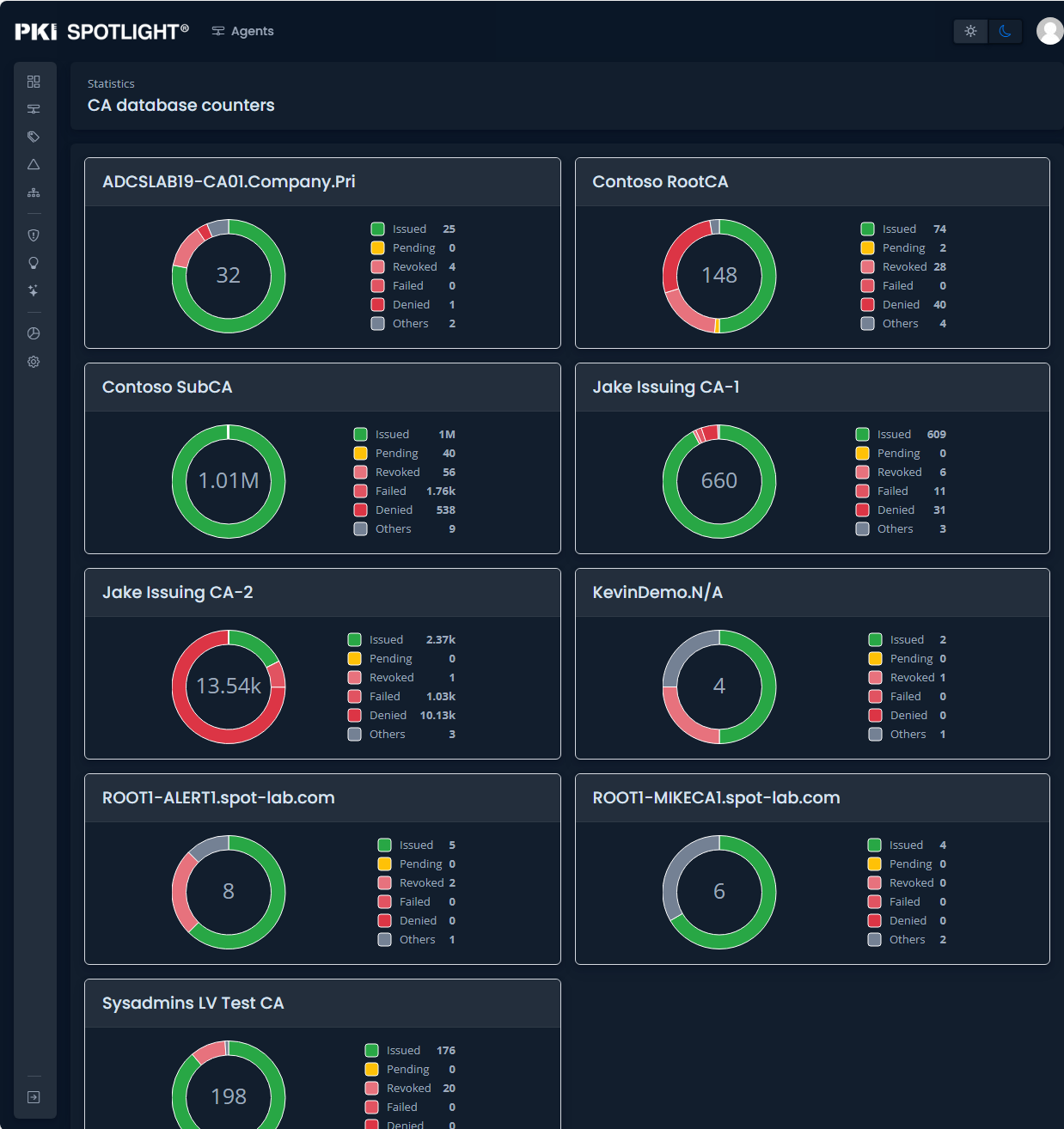
Improve Resilience and Reduce PKI Outages
Improve Resilience and Reduce PKI Outages
Detect, prevent, respond to, and recover from operational disruptions that may adversely impact your employees, customers, and suppliers to improve uptime and availability.
Learn MorePKI Threat Detection and Security Posture Management
PKI Threat Detection and Security Posture Management
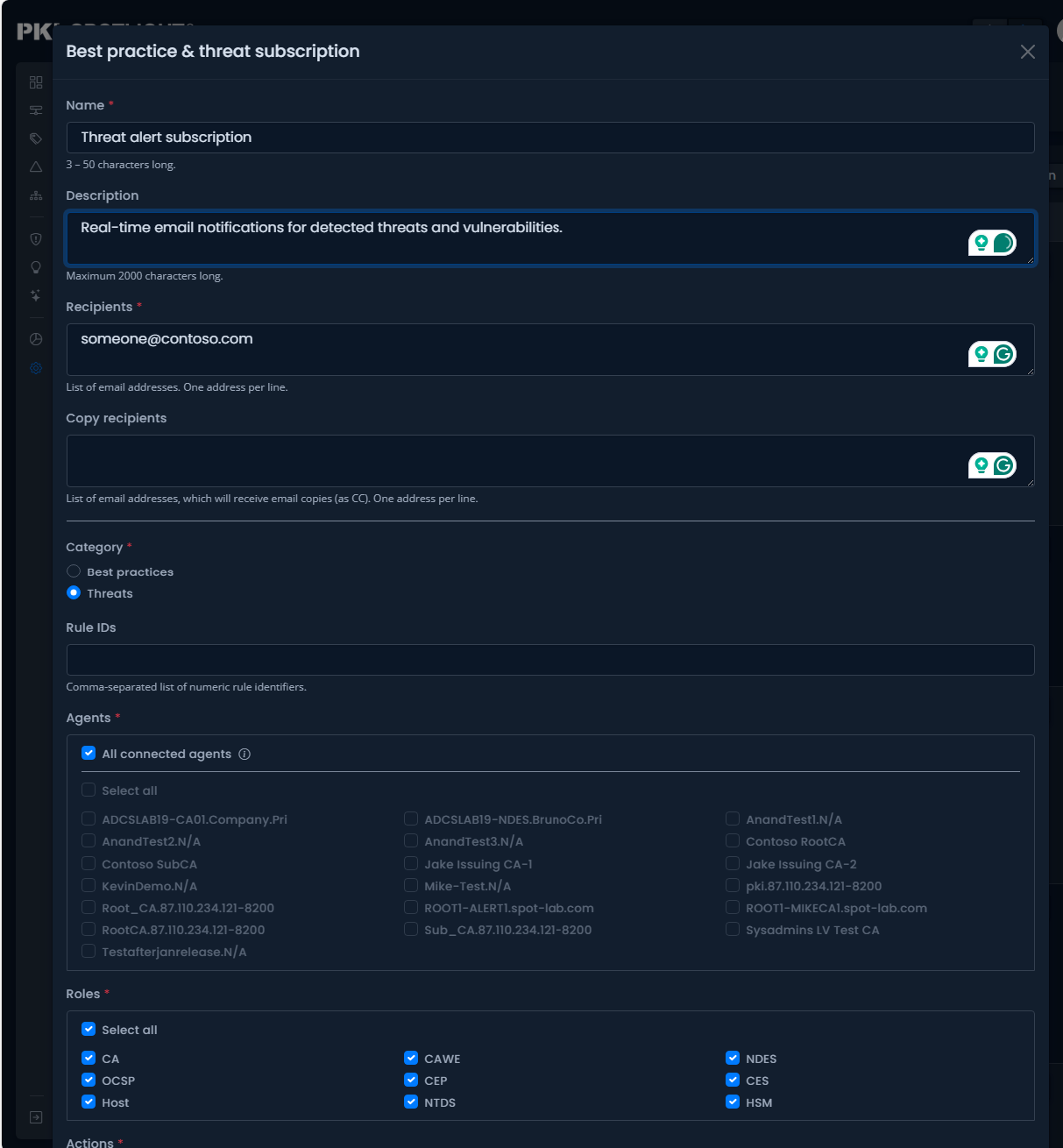
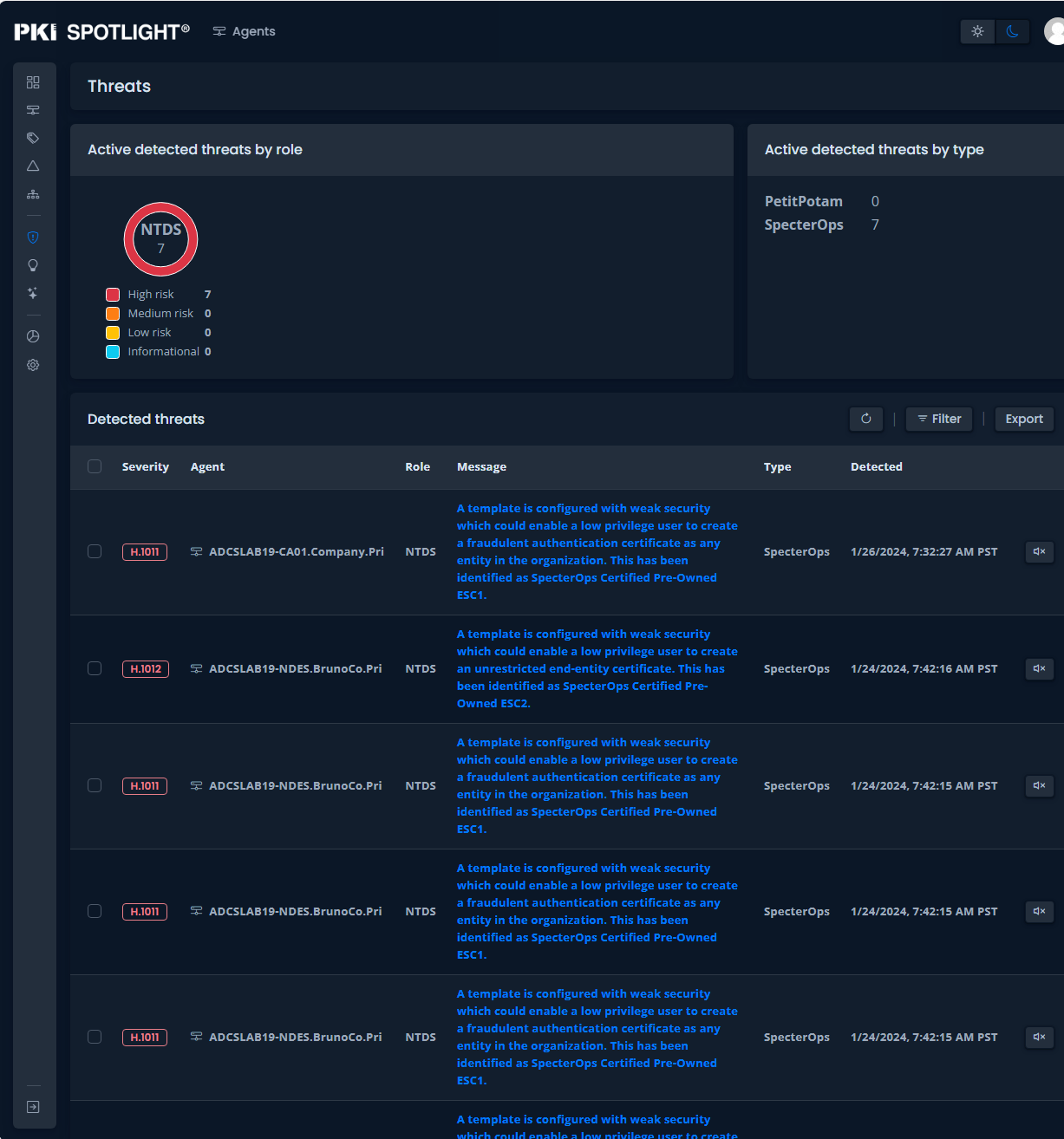
PKI Spotlight identifies and alerts of abnormal activity and threats to your PKI environments such as PetitPotam, SpecterOps Certified Pre-Owned, and more. Have you identified PKI issues in a failed penetration test? PKI Spotlight helps to remediate issues and prevent them in the future.
Learn MoreComplete Your PKI Resources for a Complete PKI Strategy
Complete Your PKI Resources for a Complete PKI Strategy
PKI Spotlight is both a comprehensive monitoring and visibility tool and a support infrastructure for reducing PKI complexity. Expand your visibility by leveraging PKI Spotlight and a CLM solution to have a holistic view across your entire PKI and certificate landscape to monitor certificate availability, issuance, and prevent outage
Find Complete PKI SupportUtilize PKI Spotlight to its Fullest with Co-Management
Managing PKI is complex. PKI Solutions supports you in your PKI ownership, elevating your team with our expert monitoring, reporting, response, remediation, and unlimited support on-demand. Contact us to learn more about our co-management for continuous support.
With Co-Management, Support is Always on Hand
-
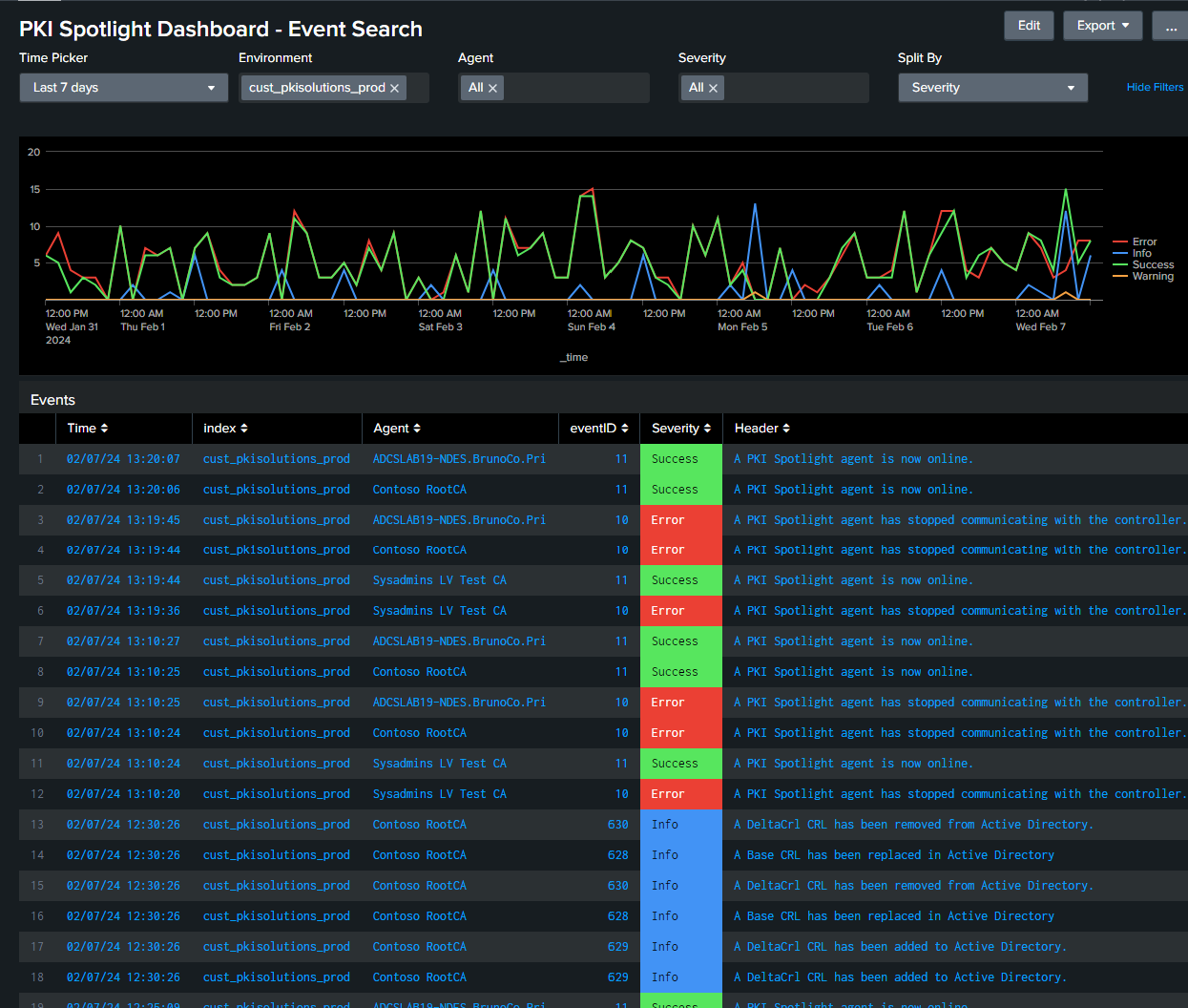
Continuous Monitoring
Businesses that don’t have dedicated resources for PKI monitoring get an extra set of eyes with co-management. Our continuous monitoring bolsters your security teams, monitoring a data feed of events and best practices alerts via Splunk, and easily integrates with your existing systems.
-
Reporting and Remediation
PKI Solutions co-management reporting supports the ease of understanding of your environment with tickets, expert investigation into root causes, and remediation strategies from the professionals who know PKI the best.
-
Support Services
With co-management, getting the customized PKI support you need is simple, efficient, and available at any time. Co-management supports your team with unlimited, timely access to expert guidance that boosts your team’s productivity, lowers operational costs, and keeps your PKI functioning.
-
Best Practices & Governance
Review, refine, and operate all of your PKIs based on industry best practices and organizational standards. PKI Solutions utilizes extensive experience in PKI scenarios to both define best practices and adapt them to your business needs.
- Security By Design: Allow security architects and PKI admins to methodically calibrate Identity, access, and encryption settings.
- Best Practices Engine: Real-time rules engine that checks against best practices to proactively recommend improvements and remediation.
- Out of the Box Recommendations: 100 and growing Out of The Box (OOTB) rules to continually check the status of PKI and HSM configurations and events against best practices
-
Operational Resilience
Operational resilience empowers organizations to adapt and thrive in unexpected challenges, showcasing their ability to navigate complexity with resilience and innovation. Spotlight PKI monitoring ensures continuous business operations, safeguards against disruptions, and enhances overall sustainability, ultimately contributing to long-term success. Operational resilience fosters a culture of preparedness and agility, allowing businesses to proactively address potential threats and maintain a competitive edge in dynamic environments.
-
Security Posture Management
PKI Spotlight provides organizations with a comprehensive and dynamic overview of their PKI (Public Key Infrastructure) landscape, allowing them to stay ahead of evolving threats and vulnerabilities. Its value lies in proactively identifying security risks, enabling a robust defense against potential cyber-attacks and data breaches. Spotlight offers real-time insights and mitigation strategies to strengthen an organization’s security posture, instill confidence among stakeholders, and maintain trust in an increasingly interconnected world.
-
Threat Detection
Our threat detection capabilities serve as a digital guardian, constantly scanning and identifying potential security risks in the complex landscape of PKI (Public Key Infrastructure). Our ability to swiftly detect abnormal activities, preventing cybercriminals from exploiting vulnerabilities and safeguarding sensitive information. Cyber threat detection is critical for maintaining the integrity of systems, networks, and data, playing a pivotal role in the ongoing battle against cyber threats and ensuring the resilience of digital ecosystems.
-
Best Practice Insights
Our best practice insights for PKI (Public Key Infrastructure) offer a systematic and practical approach to maintaining the integrity of digital certificates, bolstering the overall resilience of an organization’s cybersecurity infrastructure. Their value is apparent in providing a proactive strategy to mitigate risks, ensuring the robustness of PKI against potential threats. Best practice insights are vital in enhancing operational resilience by instilling a culture of preparedness, enabling organizations to navigate challenges confidently, and safeguarding critical cryptographic systems against disruptions.
Explore All Videos
View all videos related to PKI Spotlight features on our YouTube channel.
-
PKI Spotlight in Action: Revolutionary Tool for the Energy Industry
PKI Spotlight was born out of the critical PKI security and availability needs of the energy industry, combining the depth of our PKI expertise with the real-time visibility enterprises need. Now, the visibility that PKI Spotlight provides is critical for businesses in any industry. Learn more about how PKI Spotlight is filling the needs of energy companies and more.
- No Internet Connection: PKI Spotlight is not a SaaS solution and does not require an Internet connection. It is designed so electrical companies can run it in an isolated network.
- Best Practices and Governance: Review and refine your PKI operational and configuration practices within standard frameworks like NAESB.
- Optimal Visibility: Reduce time to solution with real-time monitoring and centralized visibility.
- Operational Resilience: Improve the uptime, availability, and recoverability of your PKIs and Hardware Security Modules (HSM) environments.
Custom PKI Solutions Success Stories
-
PKI Spotlight is an important addition to our portfolio of products and gives us productivity gains together with peace of mind that our PKI systems are available and functional, and any service that relies on our PKI is operating smoothly and securely.
Scott Fales, Principal Network Engineer at BayPort Credit Union

Connect With Us for Certainty in Security
If you’re ready to learn more about our essential solutions for your essential PKI, reach out today. Book time with one of our specialists to discuss your needs and how we can meet and exceed your business requirements.
CONTACT US
Email: hello@pkisolutions.com
Phone: +1 (971) 231-5523
Corporate Headquarters
5331 S. Macadam Ave, Suite 330
Portland, Oregon 97239

 Schedule a Demo
Schedule a Demo