The PKI Guy explores IoT security with Doug Beattie of GlobalSign
Q&A with Doug Beattie, vice president of product management, GlobalSign
TPG: Tell us about your scalable encryption.
DB: GlobalSign is an identity services company providing cloud-based, highly scalable PKI solutions for enterprises needing to conduct safe commerce, communications, content delivery, and community interactions. Our identity and security solutions enable businesses, large enterprises, cloud-based service providers, and IoT innovators around the world to conduct secure online communications, manage millions of verified digital identities, and automate authentication and encryption. GlobalSign’s ability to meet high volume, high scale, and automated identity and security requirements for the billions of devices, people and things comprising the Internet of Things (IoT) makes us the preferred choice for the many new IoT use cases. Our inception as a public Certificate Authority (CA) in 1996 has led us to pioneer the high-volume technology that allows IoT developers to employ millions of Certificates for devices and web services at unprecedented speed and ease – as many as 3,000 per second.

Expand Your PKI Visibility
Discover why seeing is securing with revolutionary PKI monitoring and alerting.
Learn More About PKI Spotlight®TPG: What do you see as the biggest security threats to enterprises today?
DB: One of the greatest threats to enterprise security is phishing. We have seen some studies, such as a recent one from Avanan’s 2019 Global Phishing Report, which claims that one of out every 99 emails is part of a phishing attack. Enterprises focused in the energy space are particularly vulnerable to ransomware attacks. One recent example is how LockerGoga ransomware infiltrated a Norwegian energy company, Norsk Hyrdo, likely originating from a spear-phishing attack on an employee. Victims of ransomware pay dearly not just in ransom fees, but in loss of productivity due to outages as well as damaged reputations. Enterprises, especially those classified as critical infrastructure, are doubling down on cyber security training. Although awareness about how to spot a phishing attack has vastly increased, the level of sophistication of spear-phishing attacks has also increased. Knowing this, InfoSec teams are mandating the use of secure email that provides stronger assurances of the sender’s identity by binding a verified identify to an email address.
TPG: What are some of the concerns with cloud security today?
DB: While public clouds offer a lot of benefits in terms of scale, flexibility and cost savings, security is usually left as an afterthought. The assumption is that major cloud providers are following security protocols and best practices, but this is simply not the case. One needs to dig deeper and ask these IaaS providers what default data security mechanisms they provide, in transit and at rest. Traditional network-based approaches to security don’t suffice here, so companies must look at newer methods such as micro-segmentation, and data governance. Following a multi-cloud approach is also best; however, coming up with security tooling and architecture that scales across public clouds is a challenge.
Network latency, especially in manufacturing settings that could impede performance are occasionally surfaced as a concern with cloud security. Those evaluating cloud-based services should inquire about throughput and burst rate limits.
TPG: How can the industry better address IoT security?
DB: In the absence of stronger government regulation, the industry can better address IoT security by self-regulation across a given vertical and following security best practice frameworks that are based on regulations from various countries and organizations. This includes supporting and utilizing standards-based and well adopted security protocols and practices to maximize interoperability and reliability. Further, given the scale of IoT, it’s imperative that security technologies are selected that can massively scale and don’t impede performance of the devices being secured. In addition, security by design vs. bolted on afterthoughts should be a required development principle.
TPG: Tell us about PKI’s role in the IoT supply chain.
DB: PKI can be used to secure IoT devices during the manufacturing process, its supply chain as well as the distribution and delivery process. Once an IoT device is built, usually it is shipped by the manufacturer to the device maker or device contractor, or directly to customers. Unfortunately, in the process of building all these devices, the ODM or EMS now has all the plans, blueprints, and design specifications. That is a huge risk for a device maker. But the good news is there are a number of ways an IoT device maker can mitigate such problems.
For instance, a certificate can be incorporated into every device, enabling companies to carefully control the number of them being manufactured by having their CA provide only as many certificates as the number of devices that are supposed to be manufactured. In addition, using PKI enables you to verify, either during or after the manufacturing process, who is actually using the certificate. Ideally, that “who” should only be the device. This can be determined by having the device contact a trusted third-party server also called a registration authority. This can be managed by CAs, who will verify that the certificate issued and in use by the device is chained to the correct PKI hierarchy, which belongs to the specific device maker.
In addition, a CA can take the extra step of revoking the previous certificate on the IoT device and issue a new one. This process is called re-enrollment. Alternatively, there can be two types of certificates used: a “birth” certificate that forms devices’ identity, and an “operational” certificate that can be used to perform certain actions.
TPG: What is GlobalSign doing to address IoT security?
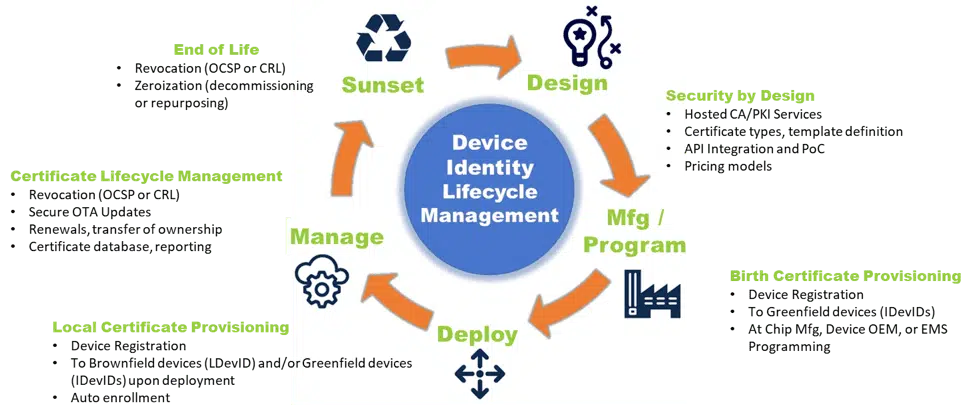
DB: GlobalSign’s history as a leading PKI provider is being leveraged strongly for the IoT. We have an ever-expanding team to meet market needs as more and more devices become connected. This is especially true for industry and manufacturing. To meet those needs, last year we launched the IoT Identity Platform, a set of products and services flexible and scalable enough to issue and manage billions of identities for IoT devices of all types. Using PKI as the core identity mechanism, the IoT Identify Platform supports the full device identity lifecycle: from initial certificate provisioning (both greenfield and brownfield deployments) to lifetime maintenance through to final sunsetting, decommissioning or transfer of ownership. Giving each device or endpoint a unique identity allows them to get authenticated when they come online and then throughout their lifetime, prove their integrity, and securely communicate with other devices, services, and users.
Security starts with device identity at the edge of the IoT and that’s where we operate by providing a means for strong and unique device identification through device certificate provisioning. We help protect the IoT from chip to cloud by protecting the identity, integrity and privacy of devices and their communication through our PKI-based IoT Identity Platform ensuring authentication, authorization and encryption.
GlobalSign provides full Device Identity Lifecycle Management. We help our clients build security into their devices, endpoints and systems by delivering hosted IoT CA/PKI services that can provision device identities. We support industry standard security-by-design practices that help secure the cloud, by securing the devices that will ultimately connect to it. We’re able to provision identities (aka birth certificates) during manufacturing (greenfield scenarios), as well as provision local operation certificates in the field at deployment (brownfield scenarios). We allow customers to manage those device certificates throughout their lifetime for renewals, transfer of ownership or to enable secure over-the-air (OTA) updates. GlobalSign IoT services manages the device certificates through sunsetting when revocation (OCSP or CRL), decommissioning or repurposing defines their end of life.
By securing endpoints from the very edge of the network with device identities we deliver authenticated, secure, and encrypted communication. We become a critical element of the network on which the device operates as it connects to the cloud.
TPG: Tell us about your certificate management solution.
DB: GlobalSign’s solution is the Auto Enrollment Gateway (AEG). It’s a fully automated, managed PKI solution that addresses scalability in the modern mixed enterprise environment. AEG integrates GlobalSign’s hosted PKI solution directly with Active Directory, enabling enterprises operating Windows environments to automate certificate provisioning and management without the burden of maintaining their own expensive and complex Internal CA. AEG acts as a connector between GlobalSign’s SaaS certificate service and an organization’s server environment, simulating aspects of an on premises CA while forwarding all certificate enrollment requests to GlobalSign. GlobalSign manages the security, high availability, and CA operations, while organizations retain control of users and policies.
TPG: How are you involved in the financial services industry?
DB: GlobalSign works with various financial services institutions and fintech companies around the world to help provide secure transactions. In particular, financial services companies look to our digital signature solutions and many are increasingly taking advantage of our digital signing service.
We are aware that this specific industry is particularly driven by regulatory developments and continuous advancement in technology. This is an exciting time for us; we see this as both a challenge and an opportunity. In particular, our European customers are looking to us for various solutions that are eIDAS compliant, which is one of the reasons GlobalSign became a Qualified Trust Service Provider (QTSP) last year. This recognition will likely lead us to increase our customer base in the financial service sector. (For readers unfamiliar with the eIDAS regulation, eIDAS is an EU regulation focused on enhancing trust in electronic transactions between citizens, businesses and public authorities cross-borders. A major component of the regulation was the creation of a common framework for secure electronic signatures, including standardized assurance levels, to facilitate interoperability and acceptance across the EU and EEA Member States. Under the law, only QTSPs can provide qualified trust services and appear on their country of operation’s Trust List. (If an entity is not on this list, it cannot provide qualified trust services.)
TPG: What is the future of passwords?
DB: Passwords are not going away anytime soon for the enterprise, but these are being augmented by two-factor, which is now the de-facto standard. However, use cases that involve remote access or privileged access will require supplemental authentication factors such as biometrics, PKI or OTPs. Further, advancements in identity and access management (IAM) will address user experience in a positive way especially around single sign-on (SSO) to both local and cloud-based applications. While adoption for facial recognition technologies remains low due to a fractured approach by various vendors (Windows Hello, Apple Face Unlock, etc.), the ease of use of this method may lead to increased adoption if a proven, secure, and consolidated method can be agreed upon.
TPG: How do you see authentication evolving over the next few years?
DB: As manufacturers of industrial control systems, factory, SCADA equipment and medical devices, in corporate connectivity into public and private networks, a host of new services will emerge as analytics mine and extract valuable data derived from these end points. Assuring the integrity of the data emanating from smart homes, cities, grids and factories will require strong endpoint authentication. We have seen the rise in newer network technologies like usage of mesh networks for IoT, low-powered networks like 6LoWPAN, as well as higher bandwidth 5G LTE networks – all endpoints on these networks will need a robust identity and authentication infrastructure. Further, network attached smart devices presents growing opportunities for hackers to spread both malware and ransomware especially through man-in-the middle attacks. Machine to Machine communication using PKI as a method to authenticate will be adopted in increasing levels to mitigate the risk of this type of spoofing. Management of identities will be as important as authentication – scalable and standard-based methods for these critical infrastructure needs will become the norm.

Mark B. Cooper
President & Founder at PKI Solutions, Leading PKI Cybersecurity Subject Matter Expert, Author, Speaker, Trainer, Microsoft Certified Master.
View All Posts by Mark B. Cooper
 Schedule a Demo
Schedule a Demo