CAB Forum Certificate Validity Updates
Since the news about changes to certificate validity was released, we have received numerous questions and observed a significant amount of misinformation stemming from misunderstandings. In this blog, our goal is to provide background information and guidance to support future planning. Specifically, we aim to clarify how the upcoming changes—shortening certificate validity periods—will impact public and private PKI-issued certificates differently.
Where The Guidelines and Updates Come From
The Certification Authority Browser Forum (CA/Browser Forum) is a voluntary gathering of Certificate Issuers and suppliers of internet browser software and other applications that use certificates (Certificate Consumers).
FAQs

Important Dates for Changing Certificate Validity Periods
| Subscriber Certificates issued before 15 March 2026 SHOULD NOT have a Validity Period greater than 397 days and MUST NOT have a Validity Period greater than 398 days. | Subscriber Certificates issued on or after 15 March 2026 and before 15 March 2027 SHOULD NOT have a Validity Period greater than 199 days and MUST NOT have a Validity Period greater than 200 days. | Subscriber Certificates issued on or after 15 March 2027 and before 15 March 2029 SHOULD NOT have a Validity Period greater than 99 days and MUST NOT have a Validity Period greater than 100 days. | Subscriber Certificates issued on or after 15 March 2029 SHOULD NOT have a Validity Period greater than 46 days and MUST NOT have a Validity Period greater than 47 days. |
Who Must Follow CAB Forum Rules?
The simple answer is only public or third-party certificates must adhere to the CAB Forum rules and guidelines.
How do systems and browsers differentiate between Public and Internal CAs
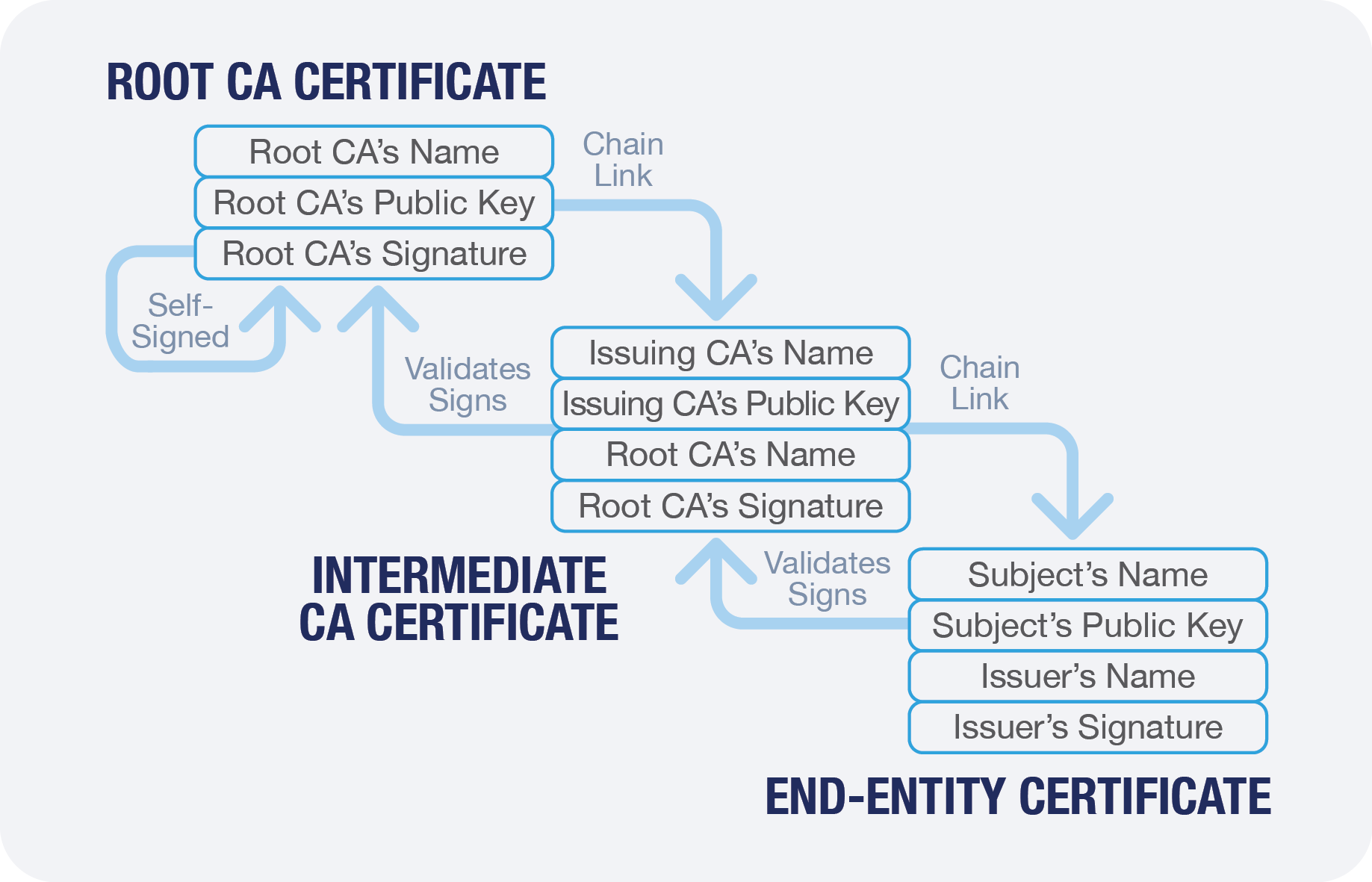
Certificate chaining, or chain building, is the process by which systems or browsers validate who issued a certificate. To trust a certificate, each certificate in the “chain” is validated based on who signed or issued it. The process is considered successful when validation reaches a root certificate that is trusted. For a root certificate to be trusted, it must be present in a system or trusted root store.
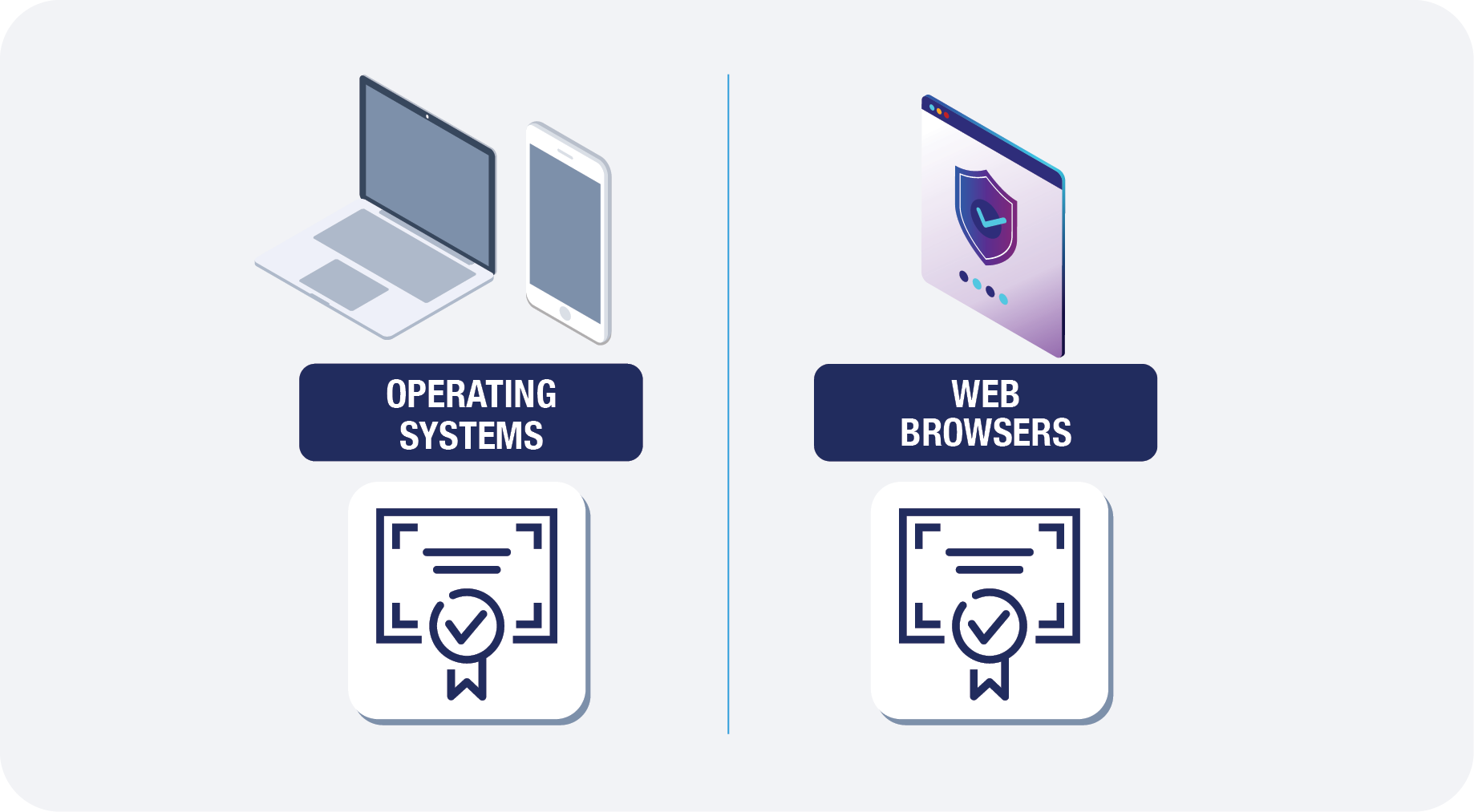
Two Types of Root CA Trust Stores
Browsers and operating systems maintain system-trusted root stores. These contain root certificates that have followed guidelines to be included with the initial install and are updated by the vendor. Organizations and end users may add root certificates to the trusted store; however, it is maintained independently from the system store.
When a browser validates a certificate via the chaining process, and it ends with a root certificate in the system’s root store, it must comply with the CAB Forum guidelines.
Certificates that chain to a root certificate added by an organization or end user are not subject to CAB Forum rules or guidelines.

Free Downloadable PDF
CAB Forum White PaperRoot CA Details and Programs
In the past, Microsoft acted as a primary authority for vetting root certificates and was relied upon by many software vendors. More recently, companies and products have chosen to create their own root CA programs. This shift is significant because organizations may now need to track multiple lists of trusted root CA certificates.
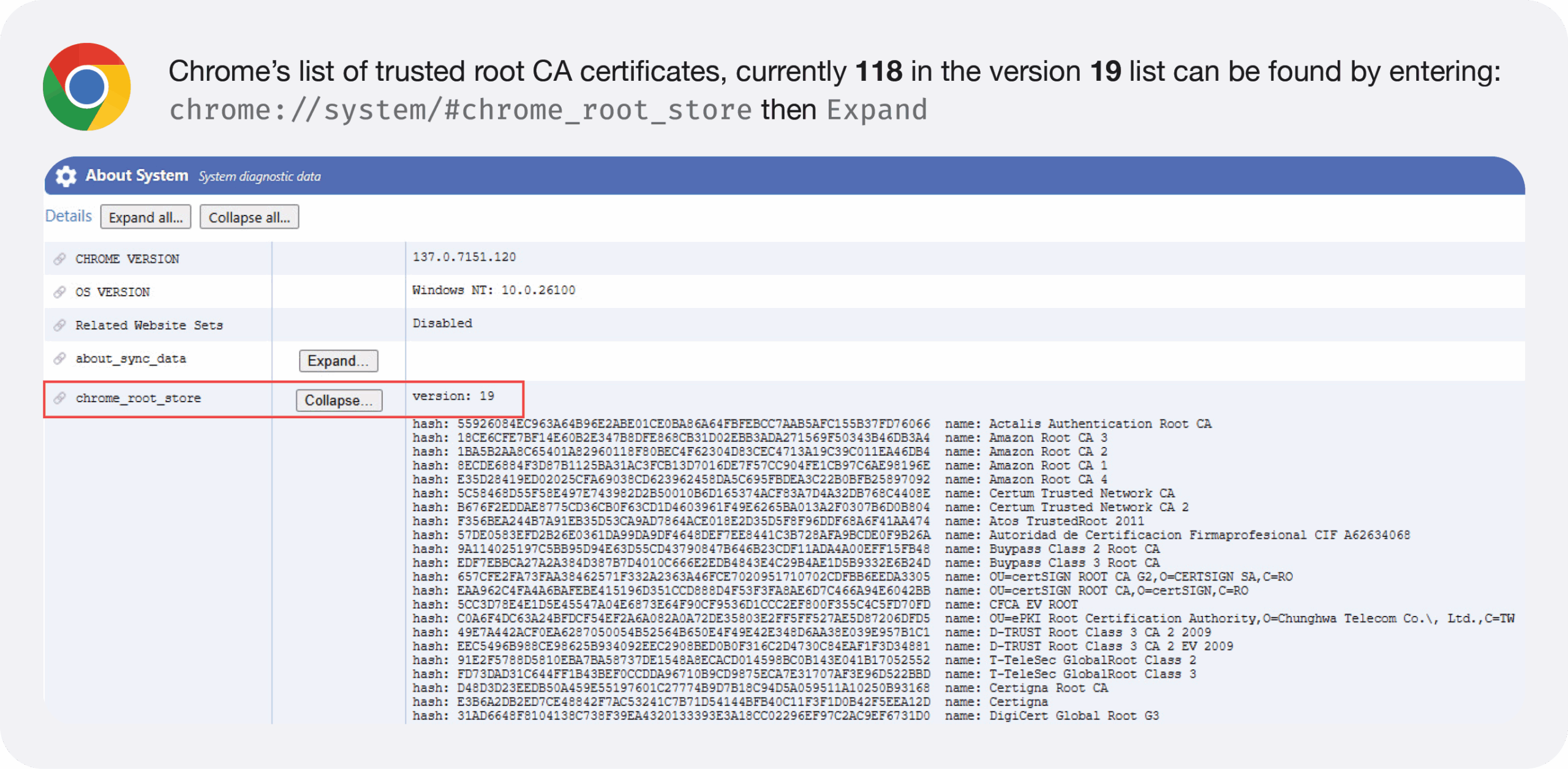
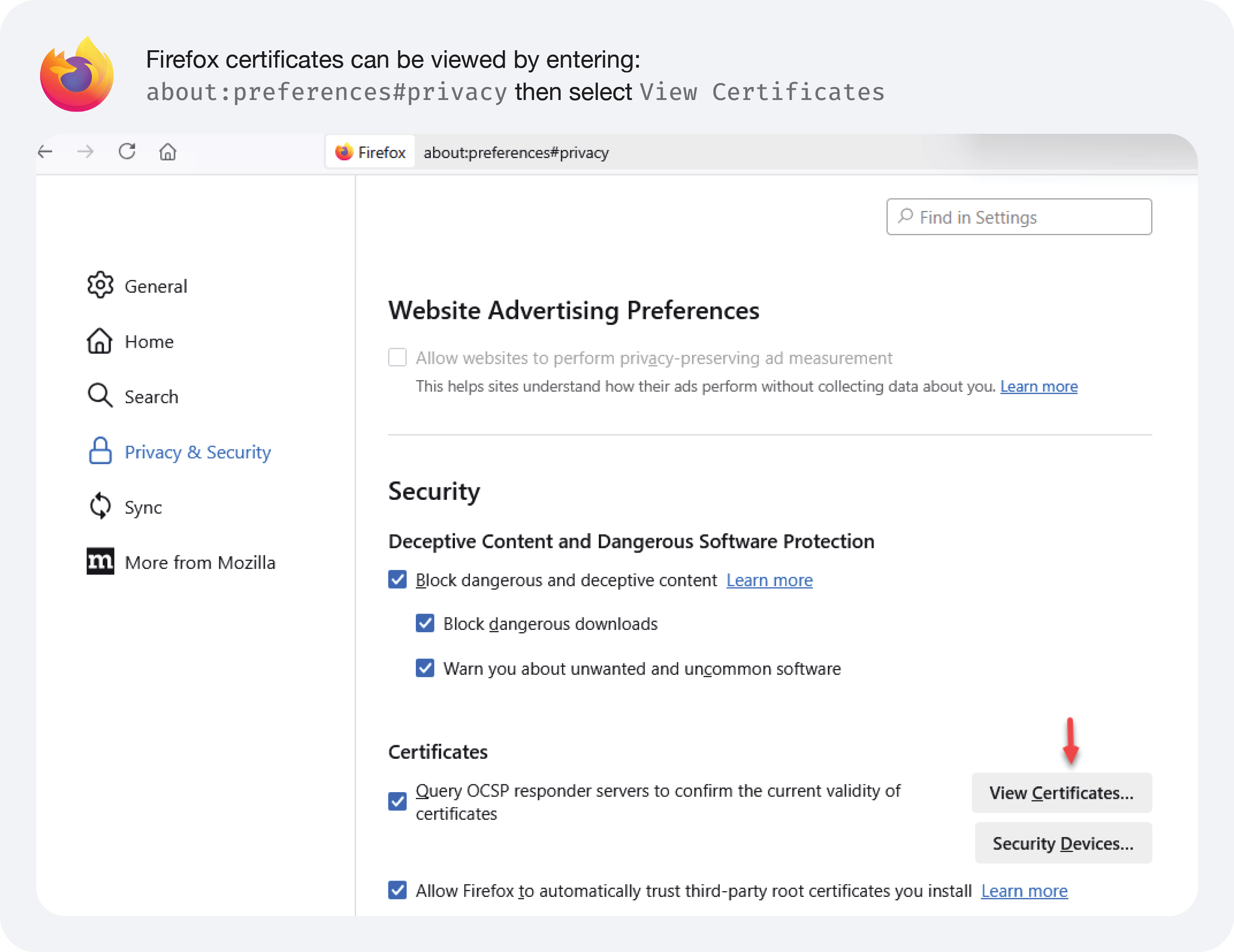
Browsers
This isn’t meant as an exhaustive list; however, it covers the majority of what our clients are using.
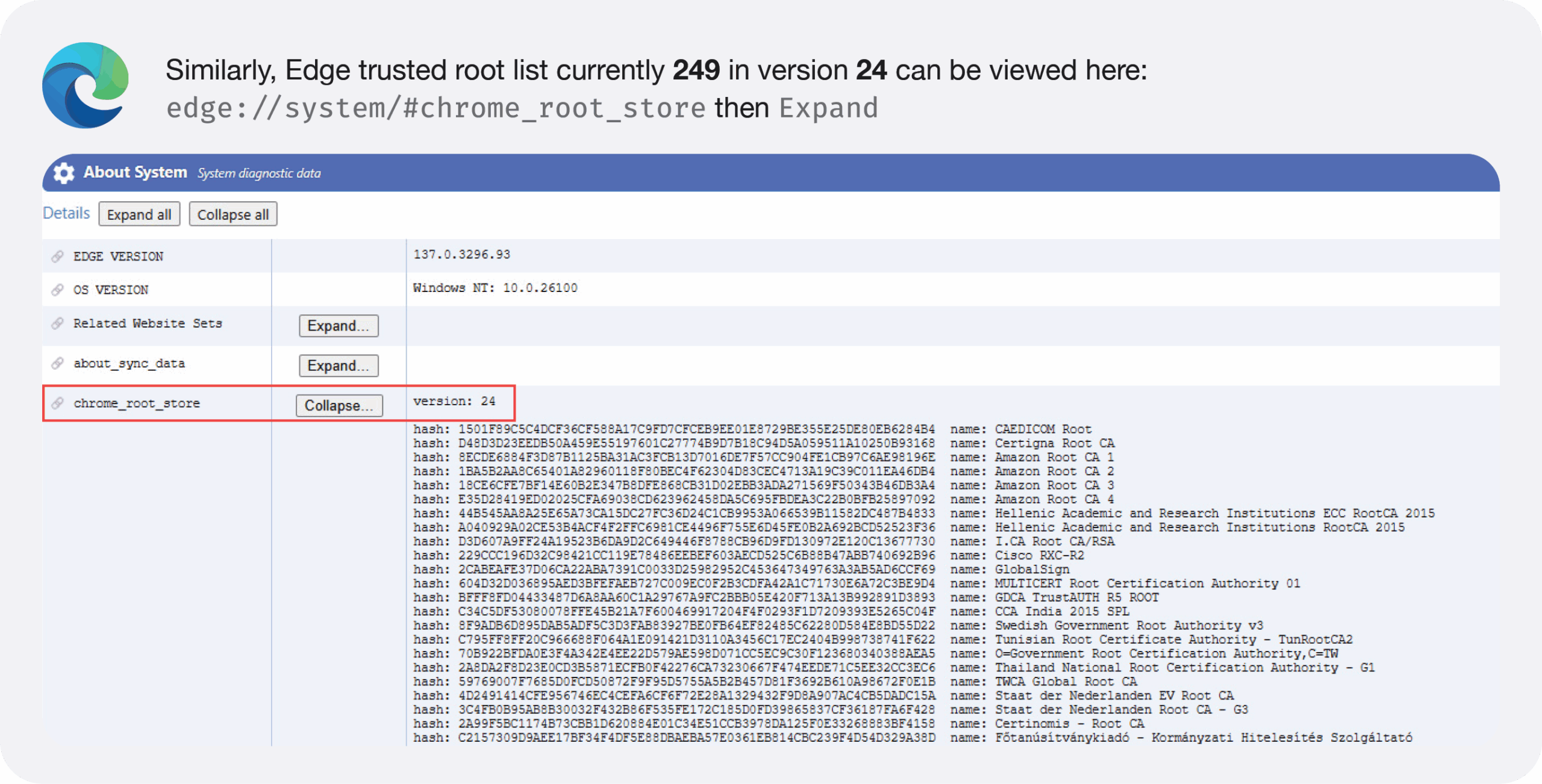
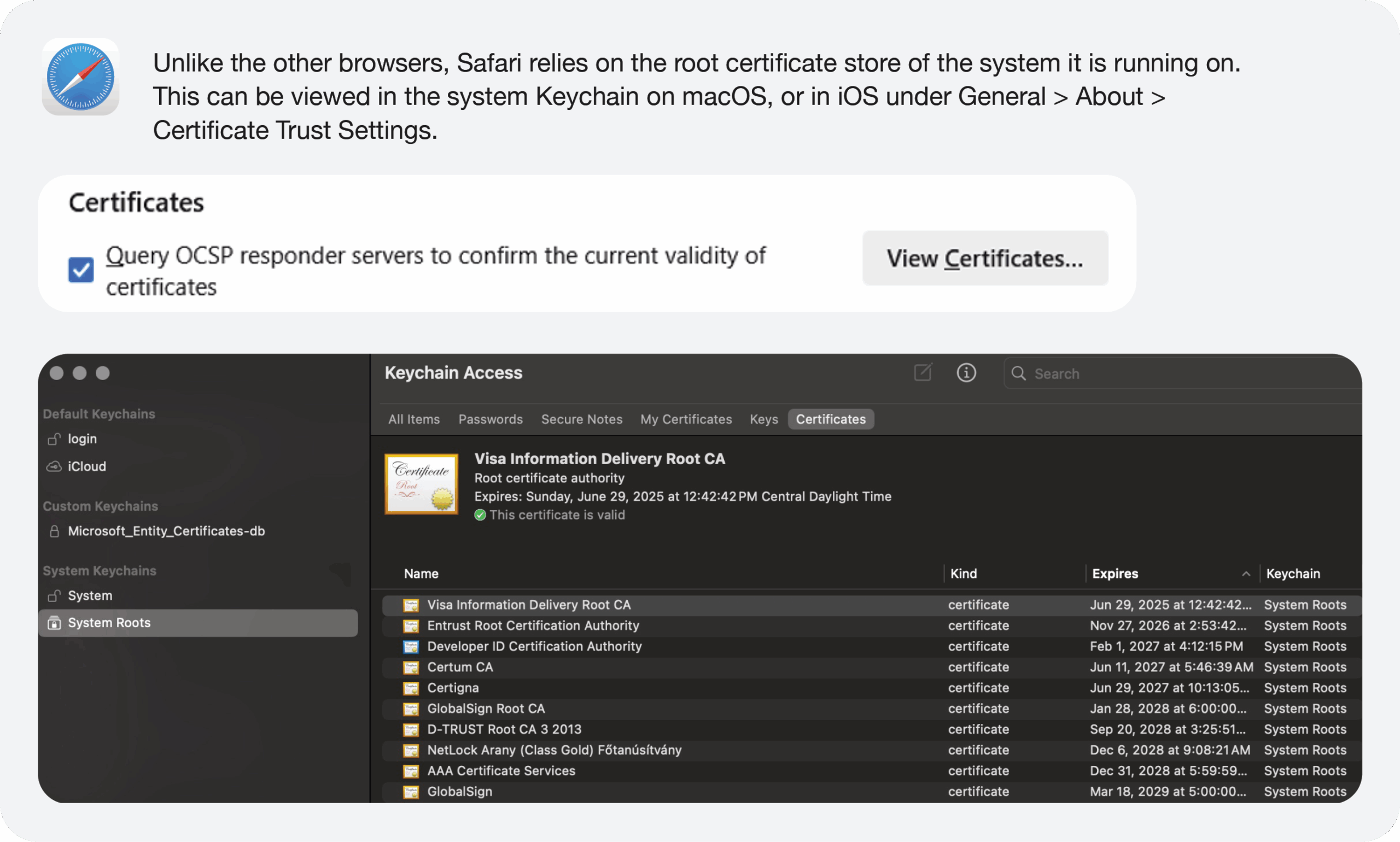
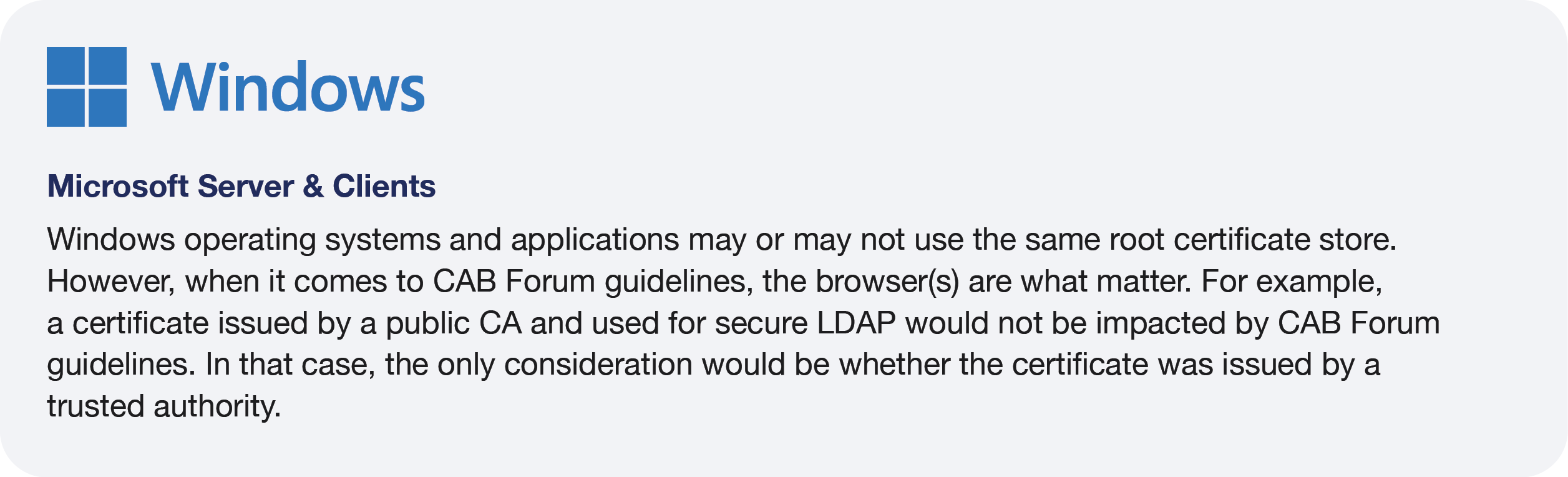
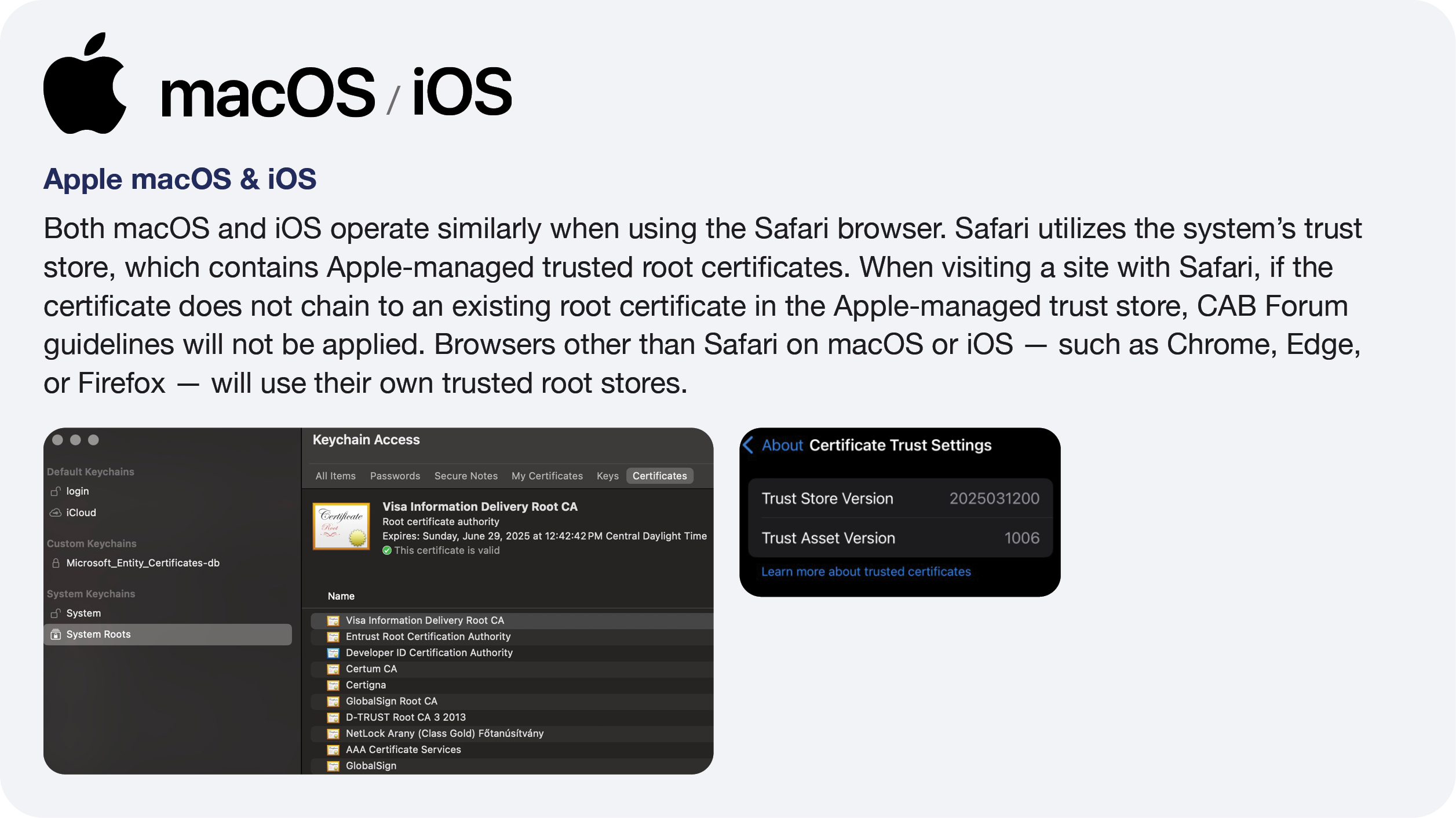
Operating Systems
Similarly to browsers, we are only covering the operating systems most of our clients use.
Summary
Hopefully, we have added clarity about which certificates the CAB Forum guidelines apply to, and when the changes can be expected. We also highlighted where the most common browsers and operating systems maintain their lists of trusted public root certificates.
This is an exciting time to be in the PKI space. Multiple changes are on the horizon, including Post-Quantum Cryptography (PQC), additional CAB Forum updates, operating system end-of-life events, and hardware security module upgrades, to name a few.
There’s a smarter way forward — and we’re here to show you how.
Stay tuned for more blogs that cut through the noise and surface what truly matters.

Take The Next Step
If you’re looking to strengthen your PKI or certificate management strategy, let’s connect and explore how our products and consulting services can support your goals.
Let's Chat
Jake Grandlienard
Jake Grandlienard brings more than 19 years of industry experience as a senior level engineer. Jake is a subject matter expert in PKI, mobile device management software, smart card management software, and Hardware Security Module (HSM) integrations.
View All Posts by Jake Grandlienard
 Schedule a Demo
Schedule a Demo